american fuzzy lop
American fuzzy lop
is a security-oriented
fuzzer
that employs a novel type of compile-time instrumentation and genetic algorithms to automatically discover clean, interesting test cases that trigger new internal states in the targeted binary. This substantially improves the functional coverage for the fuzzed code. The compact
synthesized corpora
produced by the tool are also useful for seeding other, more labor- or resource-intensive testing regimes down the road.
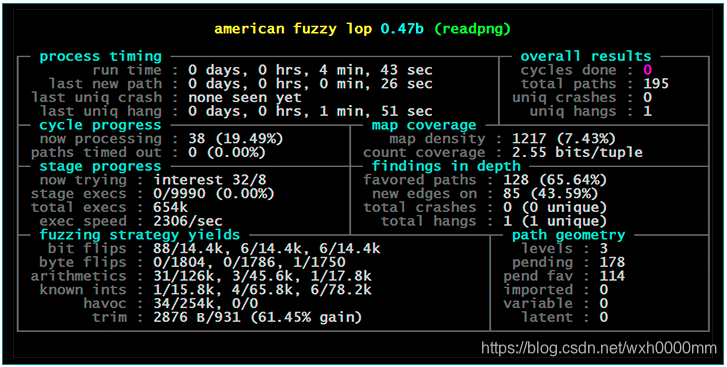
Compared to other instrumented fuzzers,
afl-fuzz
is designed to be practical: it has modest performance overhead, uses a variety of highly effective fuzzing strategies and effort minimization tricks, requires
essentially no configuration
, and seamlessly handles complex, real-world use cases – say, common image parsing or file compression libraries.
The “sales pitch”
In a hurry? There are several fairly decent reasons to give
afl-fuzz
a try:
-
It is pretty sophisticated.
It’s an instrumentation-guided genetic fuzzer capable of
synthesizing complex file semantics
in a wide range of non-trivial targets, lessening the need for purpose-built, syntax-aware tools. It also comes with a unique
crash explorer
, a
test case minimizer
, a
fault-triggering allocator
, and a
syntax analyzer
– making it dead simple to evaluate the impact of crashing bugs. -
It has street smarts.
It is built around a range of
carefully researched
, high-gain test case preprocessing and fuzzing strategies rarely employed with comparable rigor in other fuzzing frameworks. As a result, it finds
real bugs
. -
It is fast.
Thanks to its low-level compile-time or binary-only instrumentation and
other optimizations
, the tool offers near-native or better-than-native fuzzing speeds against common real-world targets. The newly-added
persistent mode
allows for exceptionally fast fuzzing of many programs with the help of minimal code modifications, too. -
It’s rock solid.
Compared to other instrumentation- or solver-based fuzzers, it has remarkably few gotchas and failure modes. It also comes with robust, user-friendly problem detection that guides you through any potential hiccups. -
No tinkering required.
In contrast to most other fuzzers, the tool requires essentially no guesswork or fine-tuning. Even if you wanted to, you will find virtually no knobs to fiddle with and no “fuzzing ratios” to dial in. -
It’s chainable to other tools.
The fuzzer generates superior, compact test corpora that can serve as a seed for more specialized, slower, or labor-intensive processes and testing frameworks. It is also capable on on-the-fly corpus synchronization with any other software. -
It sports a hip, retro-style UI.
Just scroll back to the top of the page. Enough said.
Want to try it out? Check out the
documentation
or grab the
source code
right away; there is also a single-page
quick start guide
. Still unconvinced? Have a look at the
technical whitepaper
to see what makes AFL tick.
The bug-o-rama trophy case
Yeah, it finds bugs. I am focusing chiefly on development and have not been running the fuzzer at a scale, but here are some of the notable vulnerabilities and other uniquely interesting bugs that are attributable to AFL (in large part thanks to the work done by other users):
|
IJG jpeg 1 |
libjpeg-turbo 1 2 |
libpng 1 |
|
libtiff 1 2 3 4 5 |
mozjpeg 1 |
PHP 1 2 3 4 5 6 7 8 |
|
Mozilla Firefox 1 2 3 4 |
Internet Explorer 1 2 3 4 |
Apple Safari 1 |
|
Adobe Flash / PCRE 1 2 3 4 5 6 7 |
sqlite 1 2 3 4… |
OpenSSL 1 2 3 4 5 6 7 |
|
LibreOffice 1 2 3 4 |
poppler 1 2… |
freetype 1 2 |
|
GnuTLS 1 |
GnuPG 1 2 3 4 |
OpenSSH 1 2 3 4 5 |
|
PuTTY 1 2 |
ntpd 1 2 |
nginx 1 2 3 |
|
bash (post-Shellshock) 1 2 |
tcpdump 1 2 3 4 5 6 7 8 9 |
JavaScriptCore 1 2 3 4 |
|
pdfium 1 2 |
ffmpeg 1 2 3 4 5 |
libmatroska 1 |
|
libarchive 1 2 3 4 5 6 … |
wireshark 1 2 3 |
ImageMagick 1 2 3 4 5 6 7 8 9 … |
|
BIND 1 2 3 … |
QEMU 1 2 |
lcms 1 |
|
Oracle BerkeleyDB 1 2 |
Android / libstagefright 1 2 |
iOS / ImageIO 1 |
|
FLAC audio library 1 2 |
libsndfile 1 2 3 4 |
less / lesspipe 1 2 3 |
|
strings (+ related tools) 1 2 3 4 5 6 7 |
file 1 2 3 4 |
dpkg 1 2 |
|
rcs 1 |
systemd-resolved 1 2 |
libyaml 1 |
|
Info-Zip unzip 1 2 |
libtasn1 1 2 … |
OpenBSD pfctl 1 |
|
NetBSD bpf 1 |
man & mandoc 1 2 3 4 5 … |
IDA Pro [reported by authors] |
|
clamav 1 2 3 4 5 6 |
libxml2 1 2 4 5 6 7 8 9 … |
glibc 1 |
|
clang / llvm 1 2 3 4 5 6 7 8 … |
nasm 1 2 |
ctags 1 |
|
mutt 1 |
procmail 1 |
fontconfig 1 |
|
pdksh 1 2 |
Qt 1 2… |
wavpack 1 2 3 4 |
|
redis / lua-cmsgpack 1 |
taglib 1 2 3 |
privoxy 1 2 3 |
|
perl 1 2 3 4 5 6 7… |
libxmp |
radare2 1 2 |
|
SleuthKit 1 |
fwknop [reported by author] |
X.Org 1 2 |
|
exifprobe 1 |
jhead [?] |
capnproto 1 |
|
Xerces-C 1 2 3 |
metacam 1 |
djvulibre 1 |
|
exiv 1 2 |
Linux btrfs 1 2 3 4 6 7 8 |
Knot DNS 1 |
|
curl 1 2 3 |
wpa_supplicant 1 |
libde265 [reported by author] |
|
dnsmasq 1 |
libbpg (1) |
lame 1 2 3 4 5 6 |
|
libwmf 1 |
uudecode 1 |
MuPDF 1 2 3 4 |
|
imlib2 1 2 3 4 |
libraw 1 |
libbson 1 |
|
libsass 1 |
yara 1 2 3 4 |
W3C tidy-html5 1 |
|
VLC 1 2 |
FreeBSD syscons 1 2 3 |
John the Ripper 1 2 |
|
screen 1 2 3 |
tmux 1 2 |
mosh 1 |
|
UPX 1 |
indent 1 |
openjpeg 1 2 |
|
MMIX 1 |
OpenMPT 1 2 |
rxvt 1 2 |
|
dhcpcd 1 |
Mozilla NSS 1 |
Nettle 1 |
|
mbed TLS 1 |
Linux netlink 1 |
Linux ext4 1 |
|
Linux xfs 1 |
botan 1 |
expat 1 2 |
|
Adobe Reader 1 |
libav 1 |
libical 1 |
|
OpenBSD kernel 1 |
collectd 1 |
libidn 1 2 |
|
MatrixSSL 1 |
jasper 1 2 3 4 5 6 7 … |
MaraDNS 1 |
|
w3m 1 2 3 4 |
Xen 1 |
OpenH232 1… |
|
irssi 1 2 3 |
cmark 1 |
OpenCV 1 |
|
Malheur 1 |
gstreamer 1… |
Tor 1 |
|
gdk-pixbuf 1 |
audiofile 1 2 3 4 5 6 … |
zstd 1 |
|
lz4 1 |
stb 1 |
cJSON 1 |
|
libpcre 1 2 3 |
MySQL 1 |
gnulib 1 |
|
openexr 1 |
libmad 1 2 |
ettercap 1 |
|
lrzip 1 2 3 |
freetds 1… |
Asterisk 1 |
|
ytnef 1 2 3 4 … |
raptor 1 |
mpg123 1 |
|
Apache httpd 1 |
exempi 1 2 |
libgmime 1 2 3 |
|
pev 1 2 3 4 |
Linux mem mgmt 1 |
sleuthkit 1 |
|
Mongoose OS 1 |
iOS kernel 1 |
On top of this, the fuzzer helped make countless non-security improvements to core tools (
v8
,
sed
,
awk
,
make
,
m4
,
yacc
,
PHP
,
ImageMagick
,
freedesktop.org
,
patch
,
libtasn1
,
libvorbis
,
zsh
,
lua
,
ninja
,
ruby
,
busybox
,
gcrypt
,
vim
,
Tor
,
poppler
,
libopus
,
BSD sh
,
gcc
,
qemu
,
w3m
,
zsh
,
dropbear
,
libtorrent
,
git
,
rust
,
gravity
,
e2fsprogs
, etc); found security issues in all sorts of less-widespread software (e.g.,
parrot
,
lodepng
,
json-glib
,
cabextract
,
libmspack
,
qprint
,
gpsbabel
,
dmg2img
,
antiword
,
arj
,
unrar
,
unace
,
zoo
,
rzip
,
lrzip
,
libiso*
,
libtta
,
duktape
,
splint
,
zpaq
,
assimp
,
cppcheck
,
fasm
,
catdoc
,
pngcrush
,
cmark
,
p7zip
,
libjbig2
,
aaphoto
,
t1utils
,
apngopt
,
sqlparser
,
mdp
,
libtinyxml
,
freexl
,
bgpparser
,
testdisk
,
photorec
,
btcd
,
gumbo
,
chaiscript
,
teseq
,
colcrt
,
pttbbs
,
capstone
,
dex2oat
,
pillow
,
elftoolchain
,
aribas
,
universal-ctags
,
uriparser
,
jq
,
lha
,
xdelta
,
gnuplot
,
libwpd
,
teseq
,
cimg
,
libiberty
,
policycoreutils
,
libsemanage
,
renoise
,
metapixel
,
openclone
,
mp3splt
,
podofo
,
glslang
,
UEFITool
,
libcbor
,
lldpd
,
pngquant
,
muparserx
,
mochilo
,
pyhocon
,
sysdig
,
Overpass-API
,
fish-shell
,
gumbo-parser
,
mapbox-gl-native
,
rapidjson
,
libjson
,
FLIF
,
MultiMarkdown
,
astyle
,
pax-utils
,
zziplib
,
PyPDF
,
spiffing
,
apk
,
pgpdump
,
icoutils
,
msitools
,
dosfstools
,
schoco
,
MojoShader
, and so on); and is likely responsible for quite a few other things that weren’t publicly attributed to the tool.
Download & other useful links
Here’s a collection of useful links related to
afl-fuzz
:
-
Latest source tarball for the tool
(
changes
,
past releases
), -
In-depth technical details and benchmarks
(
historical notes
).
You can
follow the author on Twitter
to stay in the loop on major improvements to AFL and related news.
The tool is confirmed to work on x86 Linux, OpenBSD, FreeBSD, and NetBSD, both 32- and 64-bit. It should also work on MacOS X and Solaris, although with some constraints. It supports programs written in C, C++, or Objective C, compiled with either
gcc
or
clang
. On Linux, the optional QEMU mode allows black-box binaries to be fuzzed, too.
There are variants and derivatives of AFL that allow you to fuzz
Python
,
Go
,
Rust
,
OCaml
, GCJ Java,
kernel syscalls
, or even
entire VMs
. There is also a closely inspired in-process fuzzer
baked into LLVM
and a
a fork that runs on Windows
. Finally, AFL is one of the fuzzing engines behind
OSS-Fuzz
.
Oh – if you have
gnuplot
installed, you can use
afl-plot
to get
pretty progress graphs
.
Contact and mailing list
To send bug reports, feature requests, or chocolate, simply drop a mail to
lcamtuf@coredump.cx
.
If you’d like to compare notes with other users or get notified about major new features, you may also want to subscribe to our
mailing list
. To join, simply send an empty mail to
afl-users+subscribe@googlegroups.com
.
Your lucky number is: 20197180