为什么需要使用HTTPS
,因为HTTP不安全,当我们使用http网站时,会遭到劫持和篡改,如果采用https协议,那么
数据在传输过程中是加密的,所以黑客无法窃取或者篡改数据报文信息,同时也避免网站传输时信息泄露。
https证书:SSH协议
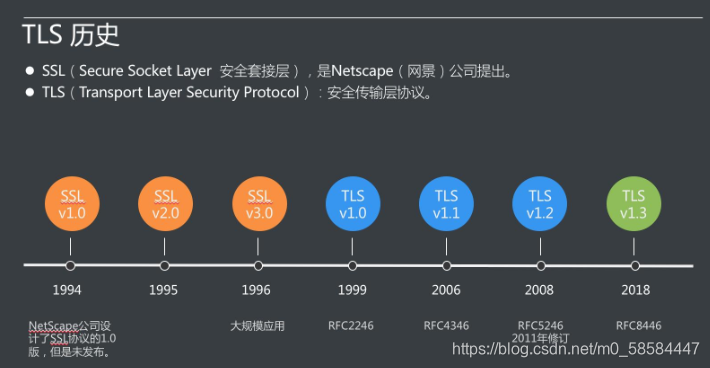
那么在数据进行加密与解密过程中,如何确定双方的身份,此时就需要有一个权威机构来验证双方身份,那么这个权
威机构就是CA机构,那么CA机构又是如何颁发证书
模拟网站被篡改
# web01上编写nginx配置文件
[root@web01 conf.d]# vim zhuzhan.conf
server {
listen 80;
server_name www.zhuzhan.com;
location / {
root /zhuzhan;
index index.html;
}
}
# 创建站点目录,编辑默认页面
[root@web01 conf.d]# mkdir /zhuzhan
[root@web01 conf.d]# vim /zhuzhan/index.html
<!DOCTYPE html>
<html lang="zh">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>这个网站要被篡改了</title>
</head>
<body>
<h1>曾老湿主站点</h1>
<img src="https://img11.51tietu.net/pic/2016-
071418/20160714181543xyu10ukncwf221991.jpg" alt="">
<p>这里是曾老湿站点 曾老湿版权所有</p>
</body>
</html># 黑客攻击
server {
listen 80;
server_name www.zhuzhan.com;
location / {
proxy_pass http://172.16.1.7;
include /etc/nginx/proxy_params;
sub_filter '<title>这个网站要被篡改了</title>' '<title>这个网站已经被篡改了
</title>';
sub_filter '<p>这里是曾老湿站点 曾老湿版权所有</p>' '<p>不是曾老湿版权所有
</p>';
sub_filter '<img src="https://img11.51tietu.net/pic/2016-
071418/20160714181543xyu10ukncwf221991.jpg" a
lt="">' '<img src="https://blog.driverzeng.com/zenglaoshi/xingganheguan.gif">';
}
}
证书的类型
|
对比 |
域名型 DV |
企业型 OV |
增强型 EV |
|---|---|---|---|
|
绿色地 址栏 |
小锁标记+https |
小锁标记+https |
小锁标记+企业名称+https |
|
一般用 途 |
个人站点和应用; 简单的 https加密需求 |
电子商务站点和应用; 中小 型企业站点 |
大型金融平台; 大型企业和政 府机构站点 |
|
审核内 容 |
域名所有权验证 |
全面的企业身份验证; 域名 所有权验证 |
最高等级的企业身份验证; 域 名所有权验证 |
|
颁发时 长 |
10分钟-24小时 |
3-5个工作日 |
5-7个工作日 |
|
单次申 请年限 |
1年 |
1-2年 |
1-2年 |
|
赔付保 障金 |
0 |
125-175万美金 |
150-175万美金 |
证书选择
保护一个域名 www
保护五个域名 www images cdn test m
通配符域名 *.xxxxx.com
https注意事项
https不支持续费,证书到期需要重新申请并进行替换 https不支持三级域名解析,如 test.m.driverzeng.com https
显示绿色,说明整个网站的url都是https的 https显示黄色,因为网站代码中包含http的不安全链接 https显示红色,
那么证书是假的或者证书过期。
单台web实现证书
# 1.查看nginx是否支持ssl证书
[root@web01 conf.d]# nginx -V
--with-http_ssl_module
# 2.创建证书的目录
[root@web01 ~]# mkdir /etc/nginx/ssl
# 3.进入证书目录
[root@web01 ~]# cd /etc/nginx/ssl
# 4.生成证书
[root@web01 ssl]# openssl genrsa -idea -out server.key 2048
Generating RSA private key, 2048 bit long modulus
............+++
..................+++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
# 5.自签证书
[root@web01 ssl]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -
keyout server.key -out server.crt
Generating a 2048 bit RSA private key
......................................................................................
.............................+++
.+++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
# 国家名,最多2个字符
Country Name (2 letter code) [XX]:CN
# 省全称
State or Province Name (full name) []:Shanghai
# 城市全称
Locality Name (eg, city) [Default City]:Shanghai
# 公司名
Organization Name (eg, company) [Default Company Ltd]:niubi
# 公司名
Organizational Unit Name (eg, section) []:niu
# 证书要保护的域名
Common Name (eg, your name or your server's hostname) []:blog.tjh.com
# 邮件
Email Address []:456798@qq.com
配置ssl证书
server {
listen 443 ssl;
server_name blog.tjh.com;
root /code/wordpress;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
}
解决问题:80强转443
vim /etc/nginx/conf.d/blog.tjh.com.conf
server {
listen 80;
server_name blog.tjh.com;
# return 302 https://$server_name$request_uri;
rewrite (.*) https://$server_name$1 redirect;
}
准备环境
|
主机名 |
外网IP |
内网IP |
角色 |
|---|---|---|---|
|
lb01 |
10.0.0.5 |
|
负载均衡 |
|
web01 |
10.0.0.7 |
172.16.1.7 |
web服务器 |
|
web02 |
10.0.0.8 |
172.16.1.8 |
web服务器 |
部署web服务器
# web01
server {
listen 80;
server_name blog.tjh.com;
root /code/wordpress;
#ssl_certificate /etc/nginx/ssl/server.crt;
#ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
index index.php index.html;
if ( -f $request_filename/index.html ){
rewrite (.*) $1/index.html break;
}
if ( -f $request_filename/index.php ){
rewrite (.*) $1/index.php;
}
if ( !-f $request_filename ){
rewrite (.*) /index.php;
}
if ($http_user_agent ~*
"Wget|ApacheBench|webBench|isouSpider|MJ12bot|YoudaoBot|Tomato|bingbot/2.0|compatible"
){
set $block_user_agent 1;
}
if ($block_user_agent = 1){
return 403;
}
}
location ~ \.php$ {
fastcgi_pass unix:/dev/shm/php71w.sock;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
# web02
server {
listen 80;
server_name blog.tjh.com;
root /code/wordpress;
#ssl_certificate /etc/nginx/ssl/server.crt;
#ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
index index.php index.html;
if ( -f $request_filename/index.html ){
rewrite (.*) $1/index.html break;
}
if ( -f $request_filename/index.php ){
rewrite (.*) $1/index.php;
}
if ( !-f $request_filename ){
rewrite (.*) /index.php;
}
if ($http_user_agent ~*
"Wget|ApacheBench|webBench|isouSpider|MJ12bot|YoudaoBot|Tomato|bingbot/2.0|compatible"
){
set $block_user_agent 1;
}
if ($block_user_agent = 1){
return 403;
}
}
location ~ \.php$ {
fastcgi_pass unix:/dev/shm/php71w.sock;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
nginx -t
systemctl reload nginx
部署负载均衡
vim /etc/nginx/conf.d/blog.conf
upstream blog_tjh_com {
server 172.16.1.7;
server 172.16.1.8;
}
server {
listen 80;
server_name blog.tjh.com;
rewrite (.*) https://$server_name$request_uri redirect;
}
server {
listen 443 ssl;
server_name blog.tjh.com;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
proxy_pass http://blog_tjh_com;
include /etc/nginx/proxy_params;
}
}
# 创建证书存放目录
[root@lb01 ~]# mkdir /etc/nginx/ssl/
# 将证书放入证书目录中
[root@web01 ssl]# scp ./* 172.16.1.5:/etc/nginx/ssl/
[root@lb01 ~]# ll /etc/nginx/ssl/
total 8
-rw-r--r-- 1 root root 1415 Aug 6 19:53 server.crt
-rw-r--r-- 1 root root 1708 Aug 6 19:53 server.key
HTTPS导致wordpress破图
原因:前端使用443端口,web使用80端口,PHP程序走的80请求
解决方法:让PHP程序知道,前端使用的是443端口
location ~ \.php$ {
fastcgi_pass unix:/dev/shm/php71w.sock;
# 告诉PHP走443端口
fastcgi_param HTTPS on;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
SSL优化参数
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 1440m;
ssl_ciphers ECDHE-RSA-AES128-GCM-
SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
blog配置优化
upstream blog_tjh_com {
server 172.16.1.7;
server 172.16.1.8;
}
server {
listen 80;
server_name blog.tjh.com;
rewrite (.*) https://$server_name$request_uri redirect;
}
server {
listen 443 ssl;
server_name blog.tjh.com;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
proxy_pass http://blog_tjh_com;
include /etc/nginx/proxy_params;
}
}
版权声明:本文为m0_58584447原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接和本声明。