SSL Version 2 and 3 Protocol Detection and TLS Version 1.1 Protocol Deprecated and TLS Version 1.0 Protocol Detection
操作系统版本:Windows Server 2012 R2
前言:若原有使用TLS1.2版本,则注册表修改后即可生效,若原有未使用TLS1.2版本但封禁了可使用的SSL/TLS版本,则会导致SSL/TLS连接无法建立,重启后方生效。
SSL Version 2 and 3 Protocol Detection
Description
The remote service accepts connections encrypted using SSL 2.0 and/or SSL 3.0. These versions of SSL are affected by several cryptographic flaws, including:
-An insecure padding scheme with CBC ciphers.
-Insecure session renegotiation and resumption schemes.
An attacker can exploit these flaws to conduct man-in-the-middle attacks or to decrypt communications between the affected service and clients.
Although SSL/TLS has a secure means for choosing the highest supported version of the protocol (so that these versions will be used only if the client or server support nothing better), many web browsers implement this in an unsafe way that allows an attacker to downgrade a connection (such as in POODLE). Therefore, it is recommended that these protocols be disabled entirely.
NIST has determined that SSL 3.0 is no longer acceptable for secure communications. As of the date of enforcement found in PCI DSS v3.1, any version of SSL will not meet the PCI SSC’s definition of ‘strong cryptography’.
Solution
Consult the application’s documentation to disable SSL 2.0 and 3.0.
Use TLS 1.2 (with approved cipher suites) or higher instead.
See Also
https://www.schneier.com/academic/paperfiles/paper-ssl.pdf
http://www.nessus.org/u?b06c7e95
http://www.nessus.org/u?247c4540
https://www.openssl.org/~bodo/ssl-poodle.pdf
http://www.nessus.org/u?5d15ba70
https://www.imperialviolet.org/2014/10/14/poodle.html
https://tools.ietf.org/html/rfc7507
https://tools.ietf.org/html/rfc7568
Output
- SSLv3 is enabled and the server supports at least one cipher.
Explanation: TLS 1.0 and SSL 3.0 cipher suites may be used with SSLv3
Medium Strength Ciphers (> 64-bit and < 112-bit key, or 3DES)
Name Code KEX Auth Encryption MAC
---------------------- ---------- --- ---- --------------------- ---
EDH-DSS-DES-CBC3-SHA DH DSS 3DES-CBC(168) SHA1
High Strength Ciphers (>= 112-bit key)
Name Code KEX Auth Encryption MAC
---------------------- ---------- --- ---- --------------------- ---
DHE-DSS-AES128-SHA DH DSS AES-CBC(128) SHA1
The fields above are :
{Tenable ciphername}
{Cipher ID code}
Kex={key exchange}
Auth={authentication}
Encrypt={symmetric encryption method}
MAC={message authentication code}
{export flag}
Risk Information
Risk Factor: Critical
CVSS v3.0 Base Score 9.8
CVSS v3.0 Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSS v2.0 Base Score: 10.0
CVSS v2.0 Vector: CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C
解释说明
启用了SSL 3.0、SSL 2.0,需要在启用TLSv1.2或TLSv1.3情况下,禁用SSL 3.2、SSL 2.0,当然了,需要启用和禁用的SSL/TLS版本随时间变化。
TLS Version 1.1 Protocol Deprecated
Description
The remote service accepts connections encrypted using TLS 1.1. TLS 1.1 lacks support for current and recommended cipher suites. Ciphers that support encryption before MAC computation, and authenticated encryption modes such as GCM cannot be used with TLS 1.1
As of March 31, 2020, Endpoints that are not enabled for TLS 1.2 and higher will no longer function properly with major web browsers and major vendors.
Solution
Enable support for TLS 1.2 and/or 1.3, and disable support for TLS 1.1.
See Also
https://datatracker.ietf.org/doc/html/rfc8996
http://www.nessus.org/u?c8ae820d
Output
TLSv1.1 is enabled and the server supports at least one cipher.
解释说明
启用了TLSv1.1,需要在启用TLSv1.2或TLSv1.3情况下,禁用TLSv1.1,当然了,需要启用和禁用的SSL/TLS版本随时间变化。
TLS Version 1.0 Protocol Detection
Description
The remote service accepts connections encrypted using TLS 1.0. TLS 1.0 has a number of cryptographic design flaws. Modern implementations of TLS 1.0 mitigate these problems, but newer versions of TLS like 1.2 and 1.3 are designed against these flaws and should be used whenever possible.
As of March 31, 2020, Endpoints that aren’t enabled for TLS 1.2 and higher will no longer function properly with major web browsers and major vendors.
PCI DSS v3.2 requires that TLS 1.0 be disabled entirely by June 30, 2018, except for POS POI terminals (and the SSL/TLS termination points to which they connect) that can be verified as not being susceptible to any known exploits.
Solution
Enable support for TLS 1.2 and 1.3, and disable support for TLS 1.0.
See Also
https://tools.ietf.org/html/draft-ietf-tls-oldversions-deprecate-00
Output
TLSv1 is enabled and the server supports at least one cipher.
Risk Information
Risk Factor: Medium
CVSS v3.0 Base Score 6.5
CVSS v3.0 Vector: CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:N
CVSS v2.0 Base Score: 6.1
CVSS v2.0 Vector: CVSS2#AV:N/AC:H/Au:N/C:C/I:P/A:N
Vulnerability Information
Asset Inventory: True
解释说明
启用了TLSv1,需要在启用TLSv1.2或TLSv1.3情况下,禁用TLSv1,当然了,需要启用和禁用的SSL/TLS版本随时间变化。
操作步骤
启用和禁用相应版本SSL/TLS
通过Windows+R打开运行或在Windows Terminal、Windows PowerShell中打开注册表
regedit
添加注册表项,若不存在TLS 1.1、Server等项均可创建
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server
名称: Enabled
类型: REG_DWORD
值:1
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server
名称: Enabled
类型: REG_DWORD
值:1
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server
名称: Enabled
类型: REG_DWORD
值:0
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server
名称: Enabled
类型: REG_DWORD
值:0
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server
名称: Enabled
类型: REG_DWORD
值:0
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
名称: Enabled
类型: REG_DWORD
值:0
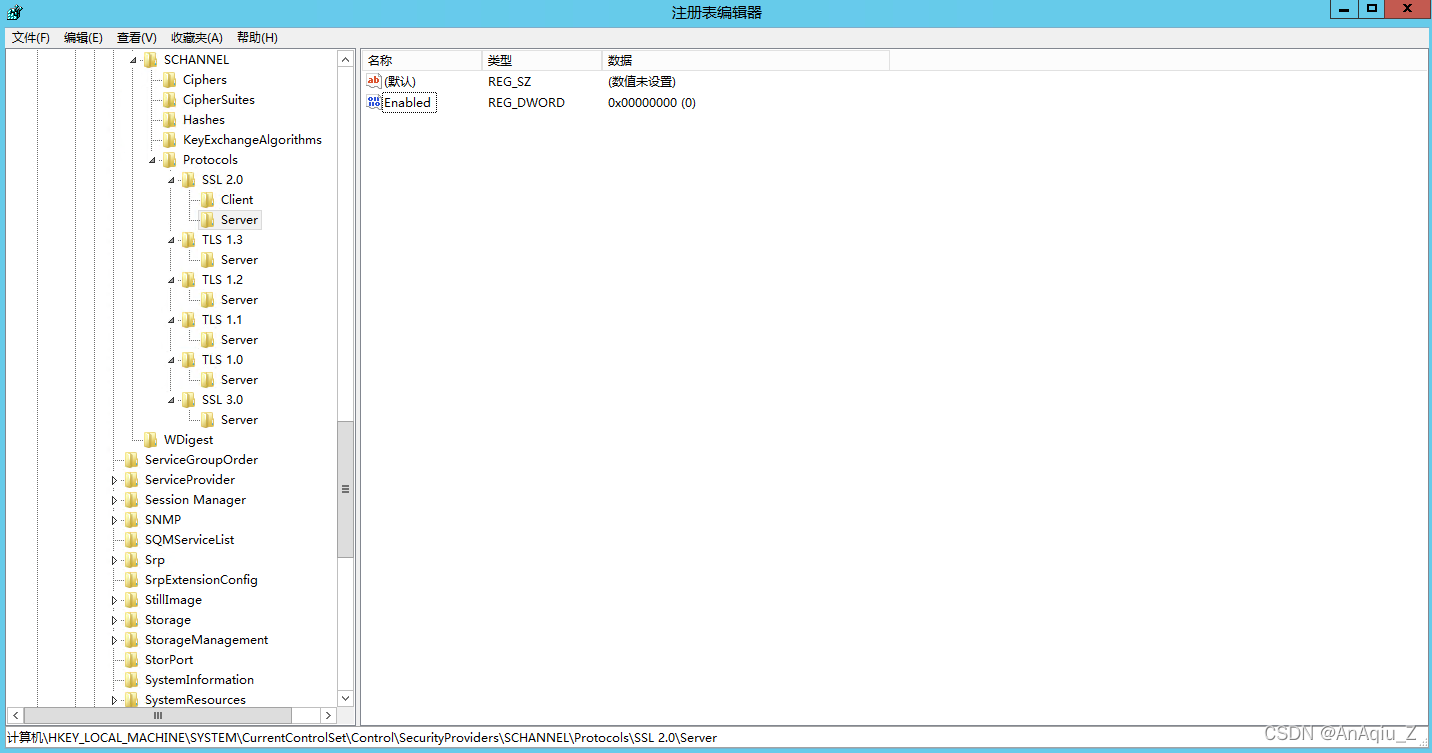
验证
因SSL/TLS连接为客户端/服务端协商建立,可通过nmap或Nessus再次扫描验证是否未出现TLS Version 1.0 Protocol Detection、TLS Version 1.1 Protocol Deprecated
参考文档:
https://docs.citrix.com/zh-cn/provisioning/current-release/advanced-concepts/limit-sql-secure-connections.html