BUUCTF-MISC-[SUCTF2018]dead_z3r0
每天一题,只能多不能少
[SUCTF2018]dead_z3r0
题目分析
1.pyc文件修复
2.pyc逆向
3.pyc隐写
开始
1.题目
解压后是个无后缀的文件,使用010editor打开
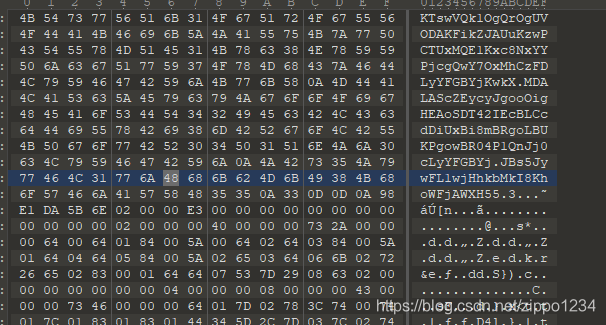
binwalk等未果
2.分析
010editor简单看一看,看到一些可疑内容
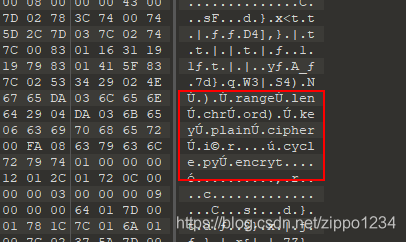

怀疑是pyc文件,但是文件头不写入了一段类似base64的东西

3.分离pyc
把从
33 0D 0D 0A
开始的复制为新的文件,保存为1.pyc

4.反编译pyc
用uncompyle6将pyc反编译,得到:
def encryt(key, plain):
cipher = ''
for i in range(len(plain)):
cipher += chr(ord(key[(i % len(key))]) ^ ord(plain[i]))
return cipher
def getPlainText():
plain = ''
with open('plain.txt') as (f):
while True:
line = f.readline()
if line:
plain += line
else:
break
return plain
def main():
key = 'LordCasser'
plain = getPlainText()
cipher = encryt(key, plain)
with open('cipher.txt', 'w') as (f):
f.write(cipher.encode('base_64'))
if __name__ == '__main__':
main()
5.逆向解密
逻辑很简单,就是跟key循环异或。那就解密之。
#!python3
# -*- coding: utf-8 -*-
# @Time : 2020/10/23 16:56
# @Author : A.James
# @FileName: tt.py
import base64
import urllib
'''
def encryt(key, plain):
cipher = ''
for i in range(len(plain)):
cipher += chr(ord(key[(i % len(key))]) ^ ord(plain[i]))
return cipher
'''
def encrypt(key, cipher):
plain = ''
cipher = base64.b64decode(cipher)
for i in range(len(cipher)):
plain += chr(ord(key[(i % len(key))]) ^ ord(cipher[i]))
return plain
'''
def getPlainText():
plain = ''
with open('plain.txt') as (f):
while True:
line = f.readline()
if line:
plain += line
else:
break
return plain
'''
def getCipherText():
cipher = ''
with open('out.txt') as f:
lines = f.readlines()
for i in range(len(lines)):
cipher += lines[i].rstrip('\n')
#print (cipher)
return cipher
'''
def main():
key = 'LordCasser'
plain = getPlainText()
cipher = encryt(key, plain)
with open('cipher.txt', 'w') as (f):
f.write(cipher.encode('base_64'))
'''
def main():
key = 'LordCasser'
cipher = getCipherText()
plain = encrypt(key, cipher)
plain = base64.b64decode(plain)
#print (plain)
print(urllib.unquote(plain))
if __name__ == '__main__':
main()
得到
y0u 4r3 f00l3d
th15 15 n0t that y0u want
90 0n dud3
c4tch th3 st3g05auru5
呵呵,被耍了。。。
6.pyc隐写
上一步解密的结果,提示了,是剑龙隐写。stegosaurus.py。
这里被坑的一逼,本人的windows环境不知道哪里抽风了,运行剑龙一直提示:
ValueError: bad marshal data (unknown type code)
搞得我怀疑人生。。最后在kali里面。秒出。。。

7.get flag
Extracted payload: SUCTF{Z3r0_fin411y_d34d}
结语
谜一样的环境问题。。。
版权声明:本文为zippo1234原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接和本声明。